Social Media
A roundup of among the handiest instruments for the gathering and evaluation of publicly accessible information from Twitter, Fb and different social media platforms
31 Might 2023
•
,
5 min. learn

Social media websites are a near-bottomless supply of data that nearly anybody can use for safety and intelligence analysis, in addition to for advertising and marketing campaigns. The platforms enable anyone to study extra about different individuals, their pursuits, experiences and affiliations, whereas organizations can simply scour the websites to realize insights about buyer sentiment or to foretell client habits.
It’s little surprise then that strategies reminiscent of Open Source Intelligence (OSINT) are more and more standard. As of late, there are quite a few instruments that automate the gathering and evaluation of public information about web customers. These strategies are additionally utilized particularly for social media intelligence, generally known as SOCMINT.
On this article, we’ll take a look at a number of instruments which will assist your social media intelligence efforts. Importantly, they’re additionally a testomony to the significance of being wary of what kind of information any of us shares online.
Namechk
Let’s begin with the simplest one. Along with checking the supply of a username on varied on-line platforms, Namechk permits you to simply seek for an individual’s on-line personas. To do that, simply enter a username and Namechk will comb via a number of on-line platforms to seek out person profiles that match the data offered. That is helpful for researchers, journalists, companies and authorities companies seeking to acquire on-line details about an individual or for individuals seeking to reconnect with long-lost buddies or acquaintances.
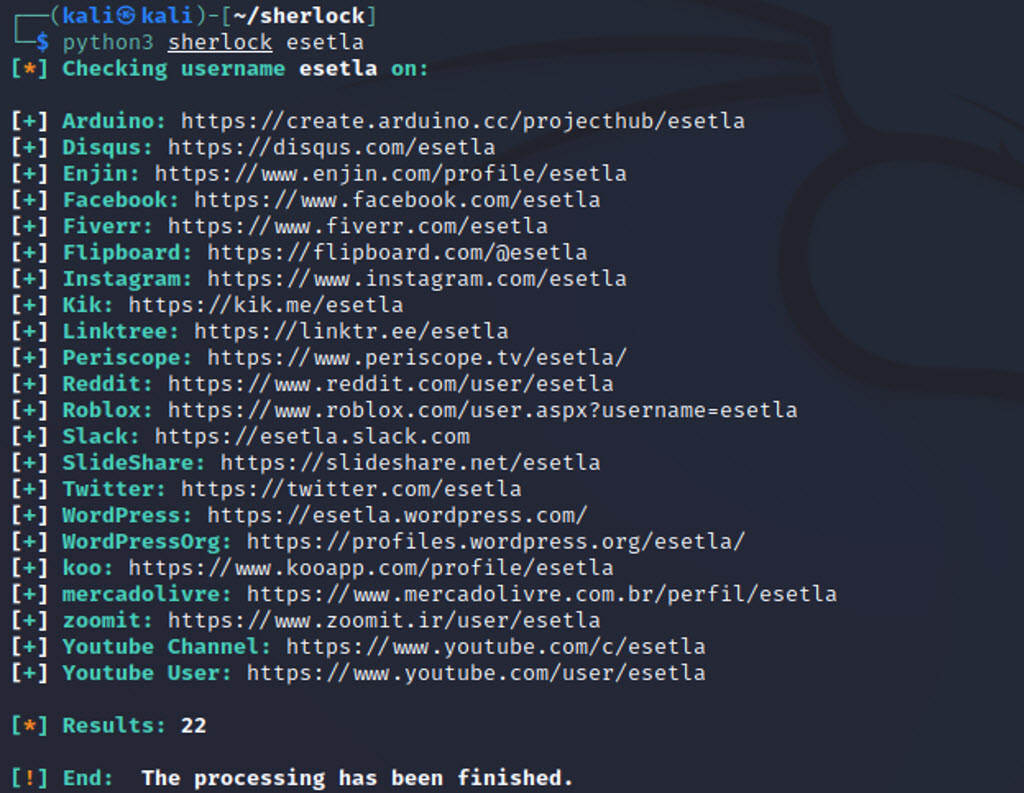
Sherlock
Sherlock is an open-source, command-line device developed in Python that, very like Namechk, searches for a specific username on the preferred social networks earlier than spitting out hyperlinks to the profiles. It has no interface and is accessed by way of a Home windows, Linux or MacOS command terminal. For extra info and set up steering, try the GitHub repository of the Sherlock Undertaking.
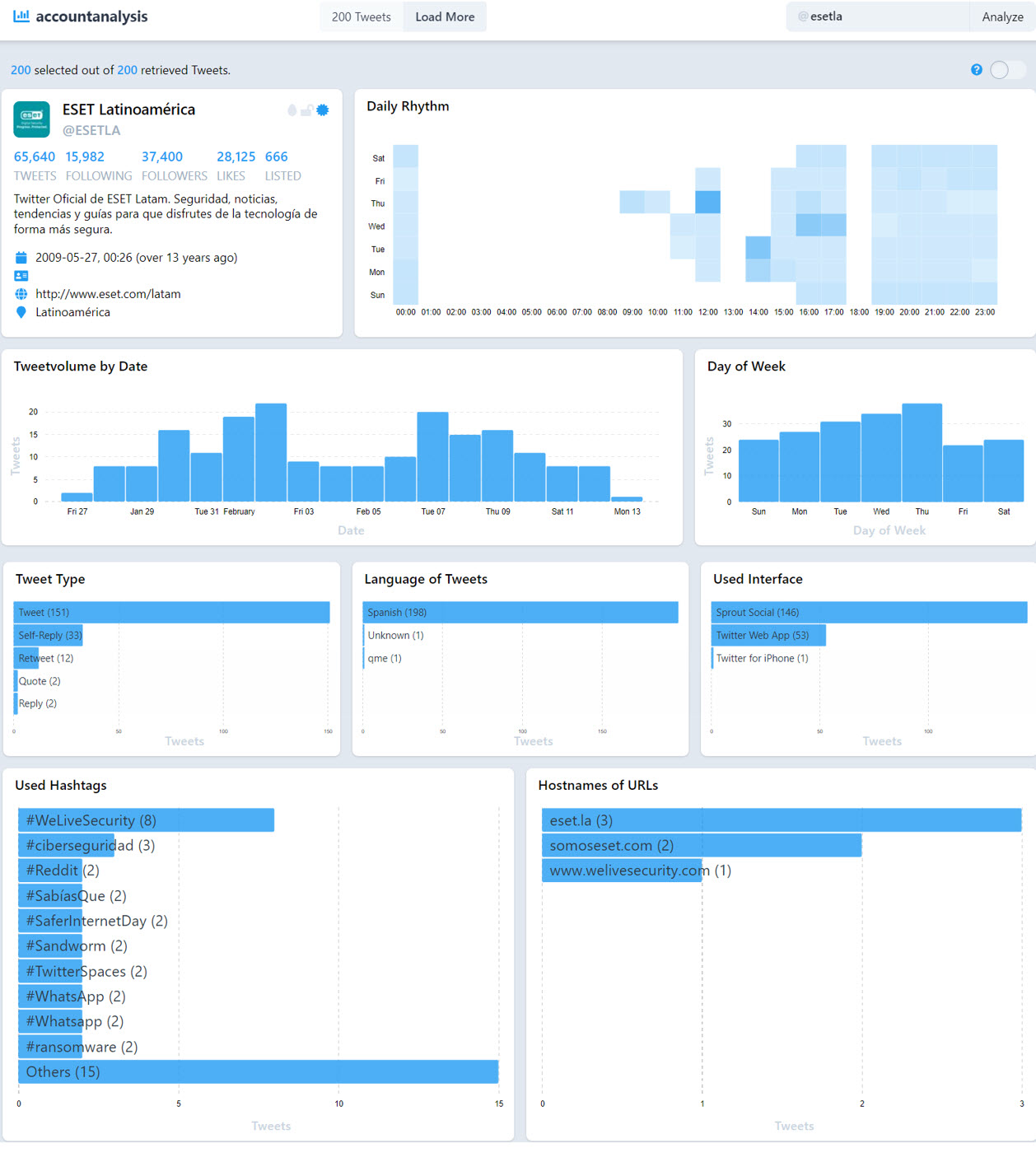
accountanalysis
accountanalysis is used to carry out OSINT analysis with a deal with Twitter. It produces a report that may be a chicken’s eye view of an account’s public info, together with its followers and adopted accounts, frequency of tweets, variety of interactions, instances of best exercise, most used hashtags and plenty of extra.
This information is beneficial to attract a wide range of conclusions: From studying extra about individuals’s tastes or opinions to checking whether or not it’s an automatic person or bot (e.g., primarily based on posting schedules) to discovering accounts which have malicious functions as a result of their selling websites with a foul repute.
Maltese
Maltego is without doubt one of the finest identified and strongest instruments within the OSINT world. It makes use of graphs to symbolize info, which lets you create relationship diagrams to determine patterns and uncover hidden connections. It additionally stands out for the variety of sources it makes use of.
Essentially the most-used options are people who make it potential to determine and visualize relationships between what the device calls entities, reminiscent of IP addresses, domains, e-mails, social community customers, and so forth. As well as, Maltego permits you to combine completely different sources of data, reminiscent of databases, on-line search instruments, APIs, and so forth.
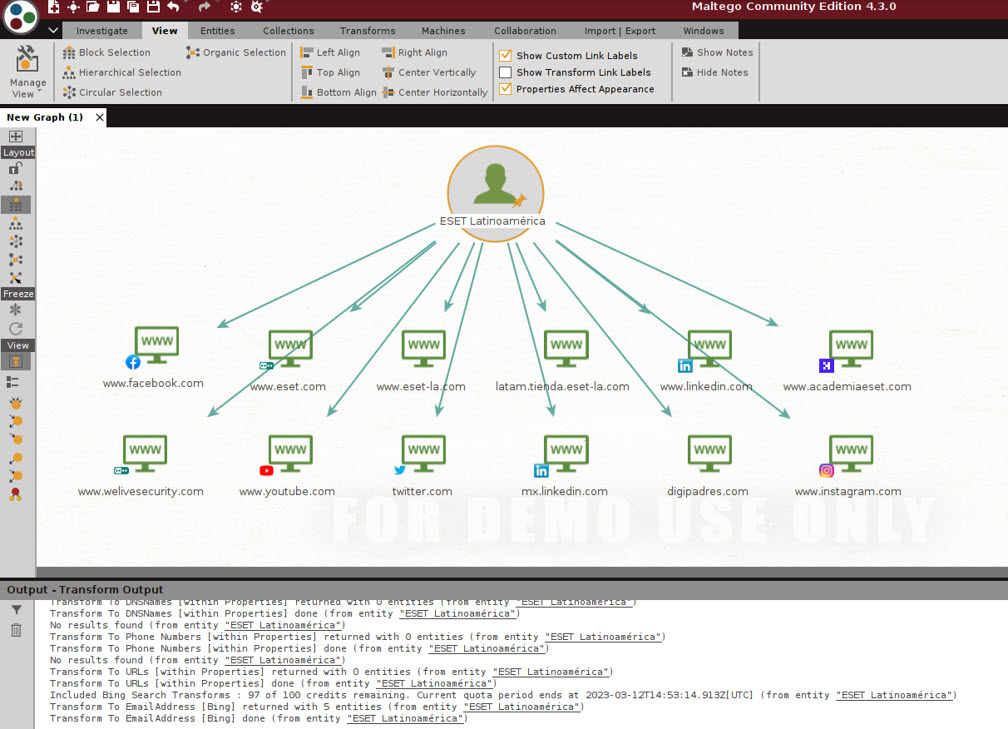
When creating a brand new graph inside the device, we are able to insert entities or already-known information in regards to the goal, reminiscent of e mail, generally used username or full identify. And with the assistance of “transforms”, Maltego will add the associated entities to the primary one.
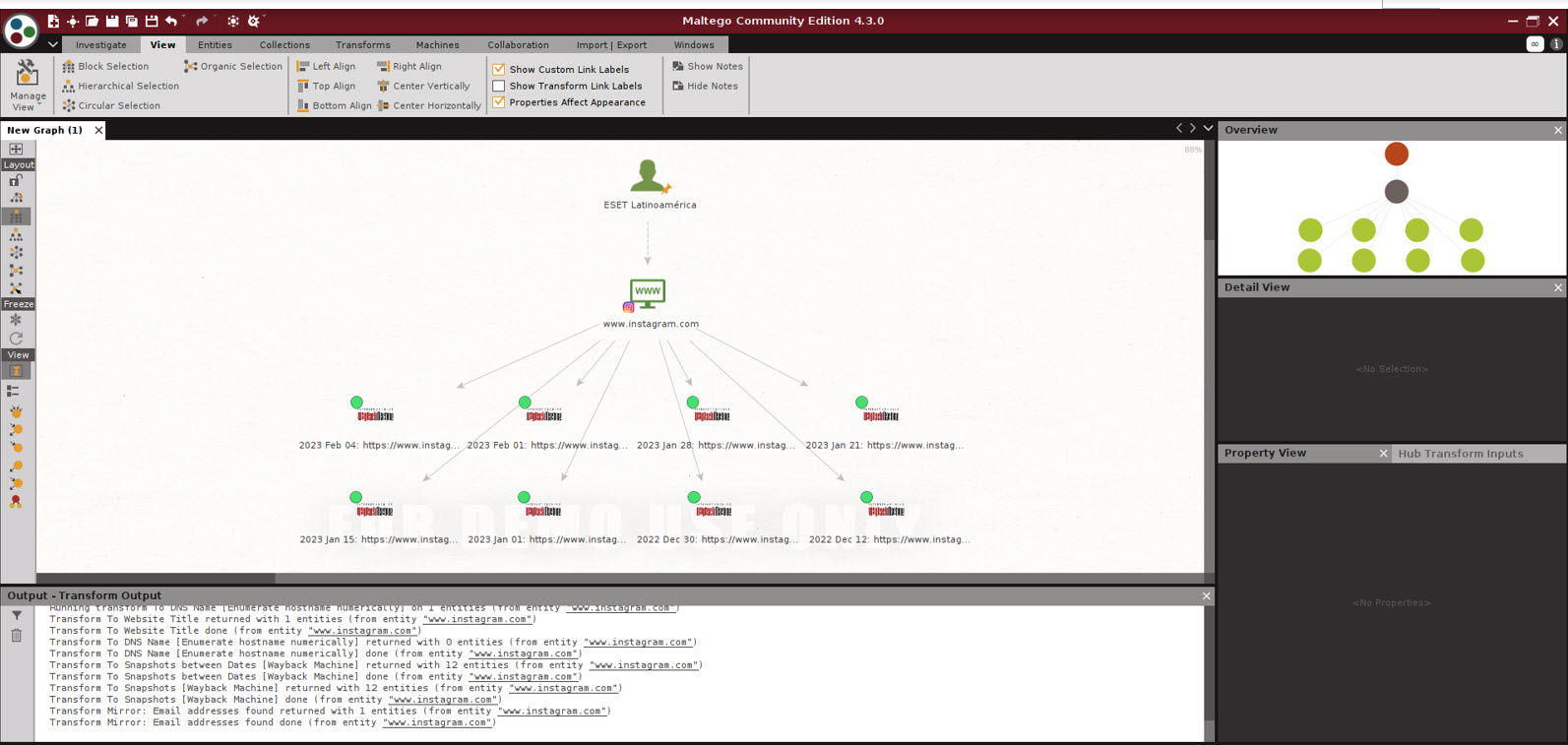
For instance, within the following picture we see some entities ensuing from a seek for “ESET Latinoamérica”. Amongst others, the device returned ESET’s social networks and associated websites, together with WeLiveSecurity.
From the newly found entities, it’s potential to re-run the transforms. The next picture reveals that digging into the ensuing Instagram profile returns recordsdata saved within the Wayback Machine.
Maltese, available for download from the official siteis a desktop utility that gives free (however restricted) licensing and limitless paid variations at each person and company ranges.
Social media as serps
Okay, this isn’t actually what you’d consider as an OSINT device, however search functionalities which are built-in inside social media websites could double as highly effective sources for intel gathering – with out leaving the app itself. That is particularly the case if the goal of your analysis is a detailed or well-known particular person. Some helpful choices are:
- Profile search: Seek for the complete identify and different related particulars of the particular person you might be researching to seek out their profile on the social community and think about their public exercise, reminiscent of their posts and shared images.
- Hashtag search: Use related hashtags to seek out posts associated to the particular person you might be researching. For instance, if you’re in search of details about an occasion, it’s potential to seek for the hashtag related to that occasion and see if the particular person has shared details about it.
- Group search: Examine if the particular person you might be researching is a member of any teams on the social community, as this will present extra details about their pursuits and actions.
- Point out search: Seek for mentions of the particular person you might be researching on the social community, to see if different persons are speaking about them and get extra details about their on-line repute and relationships.
Suggestions
When utilizing OSINT instruments, be certain that to use sure measures to make sure that the privateness and safety of people and the data collected is revered. For this reason we suggest:
- Know the regulation: It’s essential to know the native and nationwide legal guidelines and rules associated to the gathering and use of public info to make sure that you don’t commit a criminal offense or violate the privateness of others.
- Respect individuals’s privateness: It is vital to not acquire personal or confidential info with out the specific consent of the affected particular person.
- Confirm the data: You will need to confirm the truthfulness and relevance of the collected info earlier than utilizing it for any goal.
- Protect safety: When accumulating and storing info, it is very important take measures to guard it in opposition to potential theft or information breaches.
OSINT instruments for social media analysis may be very helpful, but additionally remind us of the significance of defending the data that we don’t need to be accessible or that may very well be used for malicious functions.
Watch out about what you submit on-line and keep away from oversharing details from your private life on social media.
RELATED READING:
Cleaning up your social media and passwords: What to trash and what to treasure
Attack of the Instagram clones
Facebook etiquette: Behaviors you should avoid
Using Discord? Don’t play down its privacy and security risks
Author:
Date: 2023-05-31 07:30:25