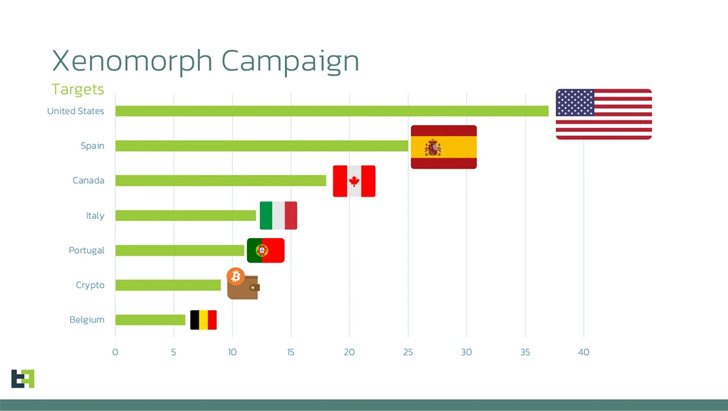
An up to date model of an Android banking trojan referred to as Xenomorph has set its sights on greater than 35 monetary establishments within the U.S.
The marketing campaign, based on Dutch safety agency ThreatFabric, leverages phishing net pages which can be designed to entice victims into putting in malicious Android apps that focus on a broader record of apps than its predecessors. A few of the different focused outstanding nations focused comprise Spain, Canada, Italy, and Belgium.
“This new list adds dozens of new overlays for institutions from the United States, Portugal, and multiple crypto wallets, following a trend that has been consistent amongst all banking malware families in the last year,” the corporate said in an evaluation printed Monday.
Xenomorph is a variant of one other banker malware referred to as Alien which first emerged in 2022. Later that yr, the monetary malware was propagated through a brand new dropper dubbed BugDropwhich bypassed safety features in Android 13.

A subsequent iteration spotted earlier this March got here fitted with options to conduct fraud utilizing what’s generally known as the Computerized Switch System (ATS).
The characteristic permits its operators, named Hadoken Safety, to utterly seize management over the machine by abusing Android’s accessibility privileges and illicitly switch funds from the compromised machine to an actor-controlled account.
The malware additionally leverages overlay assaults to steal delicate data equivalent to credentials and bank card numbers by displaying faux login screens on high of the focused financial institution apps. The overlays are retrieved from a distant server within the type of an inventory of URLs.
In different phrases, the ATS framework makes it attainable to routinely extract credentials, entry account stability data, provoke transactions, acquire MFA tokens from authenticator apps, and carry out fund transfers, all with out the necessity for any human intervention.
“Actors have put a lot of effort into modules that support Samsung and Xiaomi devices,” the researchers mentioned. “This makes sense, considering that these two combined make up roughly 50% of the whole Android market share.”
A few of the new capabilities added to the newest variations of Xenomorph embody an “antisleep” characteristic that stops the cellphone’s display screen from turning off by creating an lively push notification, an choice to simulate a easy contact at a selected display screen coordinate, and impersonate one other app utilizing a “mimic” characteristic.
Fight AI with AI — Battling Cyber Threats with Next-Gen AI Tools
Able to deal with new AI-driven cybersecurity challenges? Be part of our insightful webinar with Zscaler to deal with the rising menace of generative AI in cybersecurity.
As a solution to bypass detection for lengthy durations of time, the malware hides its icon from the house display screen launcher upon set up. The abuse of the accessibility providers additional permits it to grant itself all of the permissions it must run unimpeded on a compromised machine.
Earlier variations of the banking trojan have masqueraded as reputable apps and utilities on the Google Play Retailer. However the newest assault wave noticed in mid-August 2023 switches up the modus operandi by distributing the apps by means of counterfeit websites providing Chrome browser updates.
In an indication that the menace actors are focusing on a number of working programs, the investigation discovered that the payload internet hosting infrastructure can be getting used to serve Home windows stealer malware equivalent to Lumma C2 and RiseProin addition to a malware loader known as Private Loader.
“Xenomorph maintains its status as an extremely dangerous Android banking malware, featuring a very versatile and powerful ATS engine, with multiple modules already created, with the idea of supporting multiple manufacturer’s devices,” ThreatFabric mentioned.
Author: data@thehackernews.com (The Hacker Information)
Date: 2023-09-26 07:49:00