Hackers Report The Most Vulnerabilities In 2022 To Hold The Platform Safe
We checked out how our program carried out from February 2022 to February 2023.
In 2022, we noticed an 89% improve in bounty submissions to our program. Whereas we noticed an anticipated dip in submissions over November and December, there was vital improve from January 2023, with a 66% improve in experiences.
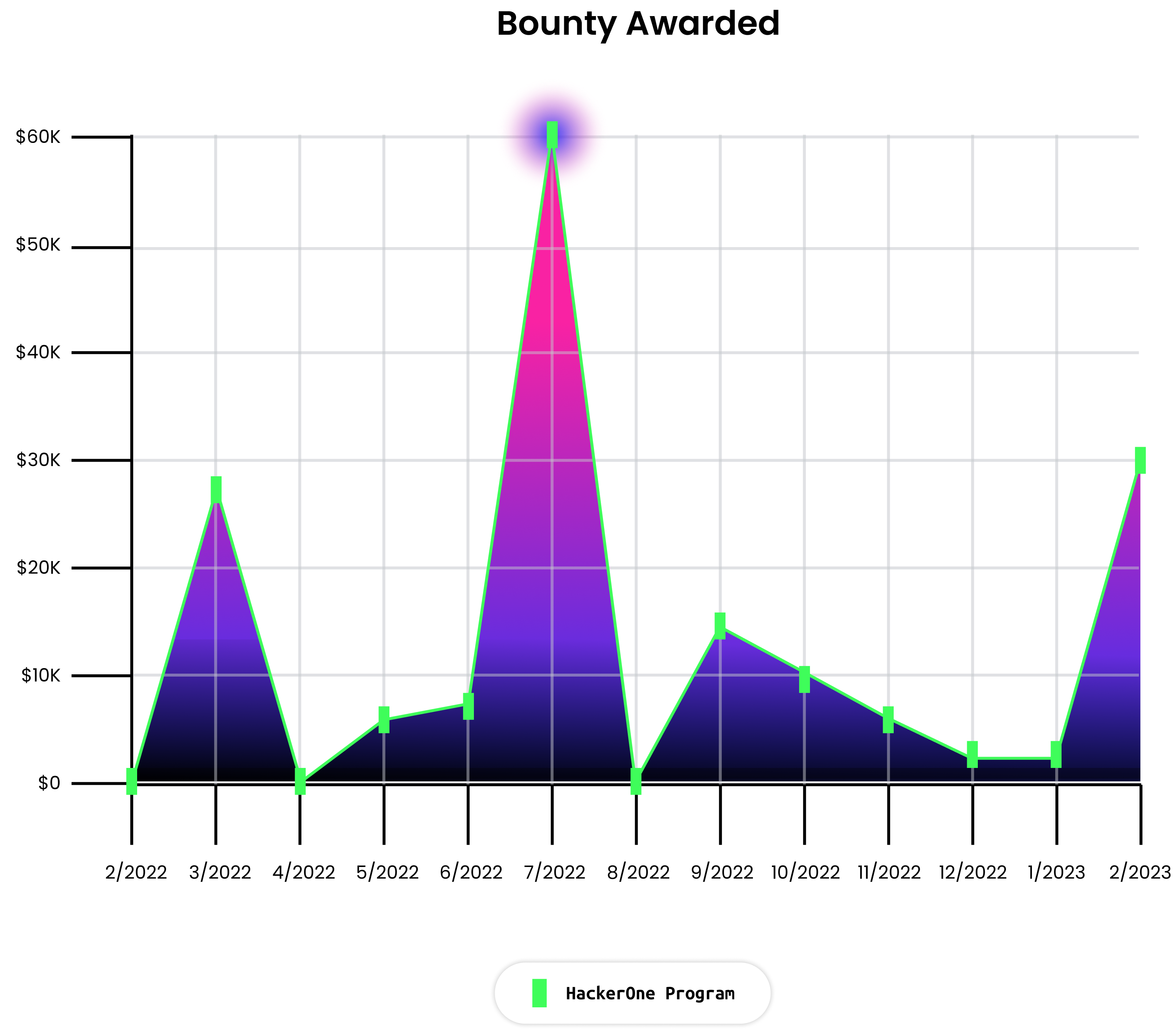
In 2022 we additionally paid out probably the most in bounty funds for our program up to now, with rewards totalling $163,134 throughout 56 findings, with a median bounty per report of $2,862. June was our most lively month, paying out over $61,000 in a single month for 143 experiences, 29 of which have been vital or excessive severity.
One measure of a mature and engaging bug bounty program is how briskly a program responds to a hacker and remediates the vulnerability. We keep a median of two days to triage a vulnerability and a month to repair it, relying on the severity. We goal to reward the hacker as near triage as potential and have a present common of 9 days till the bounty is paid.
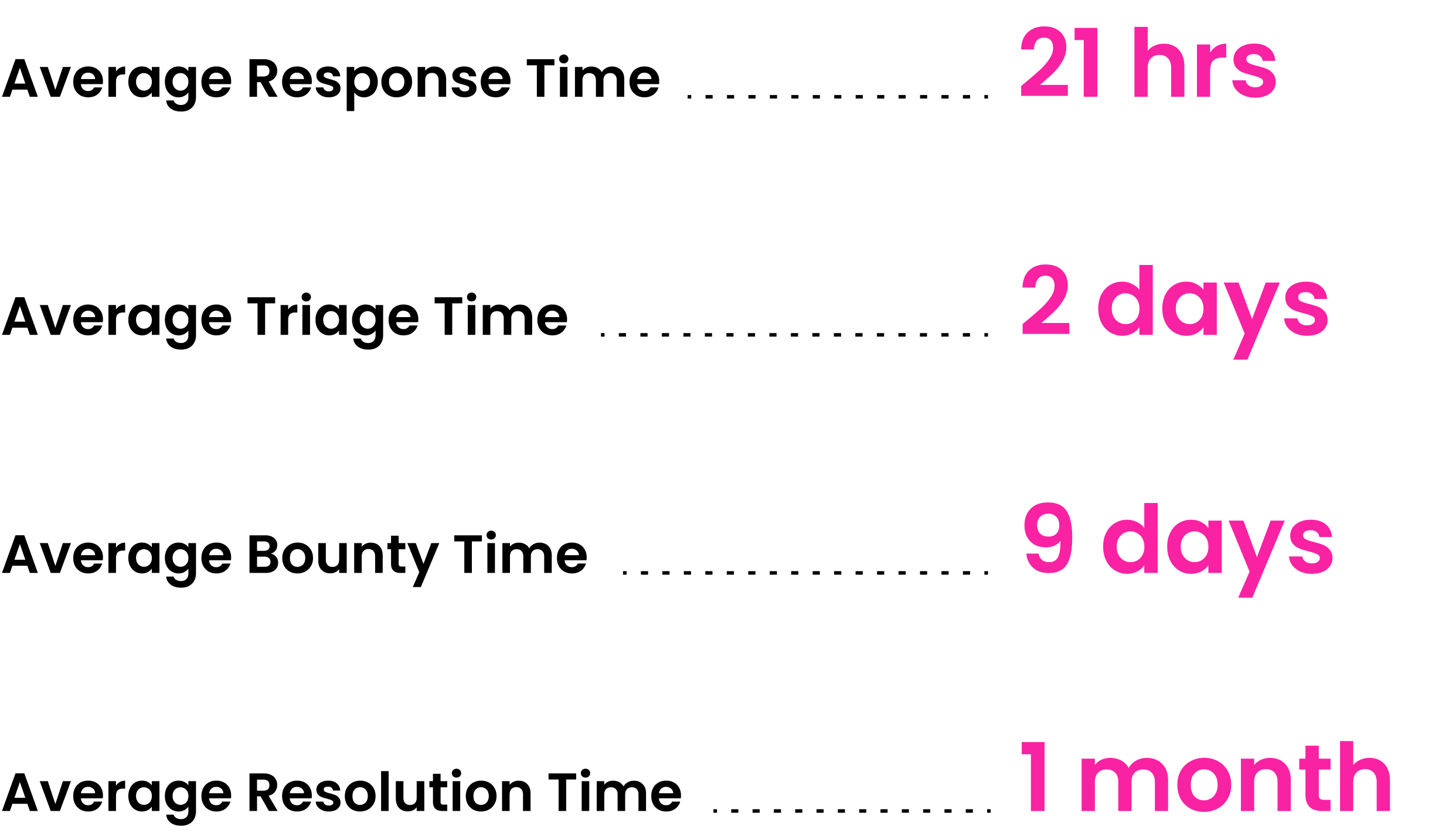
We need to lengthen particular due to the highest collaborating hackers on our program:
Acquisitions And Third Celebration Software program Flaws Have been The Largest Driver of Vulnerability Reviews
We all know that that the introduction of recent merchandise and mergers and acquisitions are specific safety dangers for our clients. Initially of 2022, we went by means of an acquisition ourselves and skilled the safety challenges that include that course of. We added PullRequest to our scope, and instantly noticed hackers report some excessive/vital finds, for instance, this blind Cross Site Scripting vulnerability within the admin portal (thanks @bugra!) And, on hackerone.com, @ahacker1 reported an a broken access control and information disclosure vulnerability within the newly launched HackerOne Property product.
We’re additionally not immune from the problem of provide chain safety and vulnerabilities present in our third social gathering suppliers. We acquired a lot of submissions that required us to work along with our distributors to repair.
Essentially the most vital third-party report was the recent ImageTragick CVEreported by @mikkocarreon, #1858574). The Native File Inclusion vulnerability in ImageMagick could be exploited when uploaded pictures are being resized. By importing a malicious PNG picture, the resizing course of will embody the native file as content material of the resized picture in a hexadecimal illustration. If exploited, an attacker may entry the server and get close to full entry to studying and altering HackerOne knowledge. Due to the bug bounty program we have been capable of patch the problem inside only a few hours of being notified. We’ll additionally publish an in depth weblog on this vulnerability within the coming months!
A specific problem with the proliferation of vulnerabilities in third social gathering know-how is that, historically, now we have solely paid 20% of the entire bounty for a vulnerability in a 3rd social gathering, that means we’re how greatest to correctly reward hackers and guarantee safety throughout two assault surfaces as we proceed in 2023.
Engineering Performs A Essential Position In Our Safety
As a HackerOne engineer, you’re anticipated to safe what you construct. Organizations are solely going to maneuver the needle on safety if builders and engineers have equal accountability for the safety of merchandise and property. As engineers, we participate in quarterly safety coaching programs to maintain knowledgeable in regards to the newest threats and easy methods to mitigate. We companion carefully with the safety group when constructing merchandise and can embody safety within the construct course of particularly when working with PII or monetary knowledge.
With regards to adopting learnings from the bug bounty program, following the preliminary triage, a rotation of engineers obtain the report, who then talk straight with the hacker, figuring out the basis trigger, triaging and escalating, or straight fixing, the vulnerability. As soon as the engineers have triaged internally, the experiences are despatched straight to the the group with probably the most context for instant validation. Having the related engineering groups examine the vulnerability and its trigger has enabled us to scale our program and improve incentives on excessive and significant severity vulnerabilities, ensuing within the improve we’ve seen this yr in excessive and significant submissions.
Lastly, we encourage our personal group submit findings to our personal program too, though these are ineligible for bounties. For instance @rcoleman discovered a SQL injection within the CVE Discovery Search and @jobert repeatedly experiences vulnerabilities on options that he’s engaged on.
Incentivizing Hackers Is The Prime Precedence in 2023
A hardened assault floor means you’re able to supply greater bounties because you’re not having to pay out for the low-hanging fruit current on a weaker assault floor and might due to this fact incentivize hackers to search out these actually vital vulnerabilities. We’ve got been experimenting with creating dynamic bounty payouts based mostly on submissions, so the bounty pot will increase the longer it takes for somebody to submit a vital vulnerability.
In 2023, we are going to proceed to iterate on our triage course of, setting clear expectations about what qualifies as a vulnerability. We see a lot of experiences shut as informative attributable to a perceived vulnerability being a characteristic fairly than a bug or as a result of it’s one thing underneath development. It’s necessary for us to be as clear as potential with researchers so everybody understands what qualifies for fee.
Experimentation is essential to creating our personal bounty program more practical and impactful and in order that we are able to move these learnings onto the client. As engineering groups increas their deal with utilizing vulnerability knowledge to construct safer merchandise, anticipate vulnerabilities to be far more durable to search out!
To learn the way to report a bug to HackerOne, take a look at our program web page: https://hackerone.com/security?type=team
Prime Suggestions For Engineers To Contribute To A Finest-In-Class Bug Bounty
Outline a transparent program – A effectively written coverage and effectively laid out scope helps hackers know the place and easy methods to function. This offers hackers the arrogance to know this system works for them.
Decrease the barrier to entry – If hackers should spend cash, or must have privileges to succeed in sure corners of your utility, they may have a more durable time testing your product. HackerOne, for instance, offers “sandbox” applications to check completely different situations with out real-world implications. Buyer applications can leverage our credentials characteristic to programatically present hackers entry to their functions.
Reward competitively – Bounty tables have a giant affect on hacker engagement. Over time, your program will get hardened and hackers want to speculate extra so as to discover vulnerabilities. Periodically elevating your bounty desk communicates that your program shouldn’t be stale. HackerOne is experimenting with an idea known as “smart rewards”: we repeatedly improve a bonus bounty pool till a vulnerability is discovered and, as soon as discovered, reset the “bonus” again to zero for an additional cycle.
Construct a relationship along with your hacker neighborhood – Be responsive. Constructive and common communication leads to quicker and higher triaging and fewer frustrations, bettering hacker retention.
Squash these bugs – With our program, now we have discovered that it’s necessary to have a strong course of to triage and hand over experiences to the proper group. Be sure you additionally request a retest to make sure the vulnerability has been resolved and to verify for any undesirable side-effects.
Go to our documentation page for extra details about operating a best-in-class program
Author: Rafael de Carvalho
Date: 2023-05-30 18:00:00



