Targets positioned in Azerbaijan have been singled out as a part of a brand new marketing campaign that is designed to deploy Rust-based malware on compromised methods.
Cybersecurity agency Deep Intuition is monitoring the operation beneath the identify Operation Rusty Flag. It has not been related to any recognized menace actor or group.
“The operation has at least two different initial access vectors,” safety researchers Simon Kenin, Ron Ben Yizhak, and Mark Vaitzman said in an evaluation printed final week. “One of the lures used in the operation is a modified document that was used by the Storm-0978 group. This could be a deliberate ‘false flag.'”

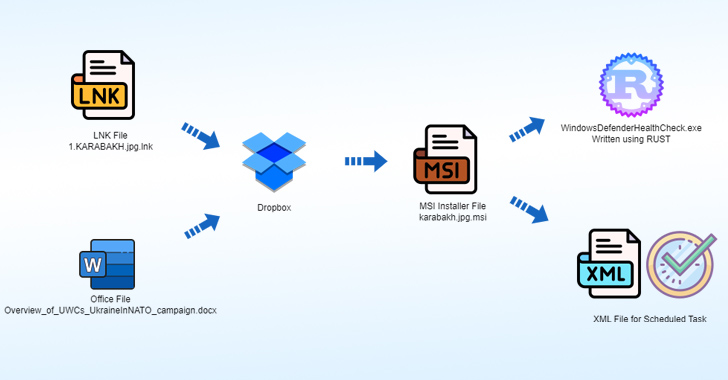
The assault chain leverages an LNK file named 1.KARABAKH.jpg.lnk as a launchpad to retrieve a second-stage payload, an MSI installer, hosted on Dropbox.
The installer file, for its half, drops an implant written in Rust, an XML file for a scheduled process to execute the implant, and a decoy picture file that options watermarks of the symbol of the Azerbaijan Ministry of Protection.
An alternate an infection vector is a Microsoft Workplace doc named “Overview_of_UWCs_UkraineInNATO_campaign.docx,” which exploits CVE-2017-11882a six-year-old reminiscence corruption vulnerability in Microsoft Workplace’s Equation Editor, to invoke a Dropbox URL internet hosting a unique MSI file serving a variant of the identical Rust backdoor.
The usage of Overview_of_UWCs_UkraineInNATO_campaign.docx is noteworthy, as a lure with the identical filename was leveraged by Storm-0978 (aka RomCom, Tropical Scorpius, UNC2596, and Void Rabisu) in latest cyber assaults focusing on Ukraine that exploit an Workplace distant code execution flaw (CVE-2023-36884).
AI vs. AI: Harnessing AI Defenses Against AI-Powered Risks
Able to deal with new AI-driven cybersecurity challenges? Be part of our insightful webinar with Zscaler to deal with the rising menace of generative AI in cybersecurity.
“This action looks like a deliberate false flag attempt to pin this attack on Storm-0978,” the researchers stated.
The Rust backdoor, one in every of which masquerades as “WinDefenderHealth.exe,” comes fitted with capabilities to assemble data from the compromised host and ship it to an attacker-controlled server.
The precise finish objectives of the marketing campaign stay unclear at this stage. On the identical time, the likelihood that it could possibly be a pink staff train has not been discounted.
“Rust is becoming more popular among malware authors,” the researchers stated. “Security products are not yet detecting Rust malware accurately, and the reverse engineering process is more complex.”
Author: information@thehackernews.com (The Hacker Information)
Date: 2023-09-19 08:05:00