Safety leaders typically battle to maintain tempo with the evolving nature of their respective assault surfaces. Many fall behind of their capacity to establish and remediate vital vulnerabilities. A corporation of superior digital maturity—one which depends on digital companies as a core competency of its enterprise—deploys new software program releases a mean of 1,460 occasions per yr, in keeping with the DORA DevOps Report. Id governance supplier SailPoint stated they’re “proud to average 60 releases each week.”
Every day and weekly agile software program releases embody bug fixes and safety patches alongside new performance. Because of this, new vulnerabilities are launched each day, whilst groups plug present safety holes. With so many software program releases, it’s important for safety leaders to grasp the frequency and cadence of the safety checks they need to be performing annually.
By benchmarking annual software safety testing cadence and frequency towards organizations of comparable measurement and digital maturity, safety leaders can set life like and achievable targets for software safety testing and transfer in the direction of closing the attack resistance gap and stopping breaches.
Our benchmarks present a place to begin to find out what number of checks (each automated scans and moral hacker-led safety assessments) your group ought to carry out yearly, relying on measurement and digital maturity.
Benchmark the Frequency and Protection of App Safety Assessments
The desk under offers a place to begin to align your group with its most applicable measurement and maturity class. Use it to find out how typically and to what diploma you have to be safety testing your app releases annually. There are two major standards: testing frequency and protection depth.
Your group ought to decide its testing frequency by the entire quantity and cadence of app releases. The suitable protection depth will depend on the criticality of the apps, knowledge sensitivity, and compliance necessities.
For instance, an “average” mid-sized brick-and-mortar retail enterprise with a digital presence would carry out month-to-month static software safety check (SAST) scans on 55% of its app releases. Evaluate this to an “advanced” giant monetary companies agency housing plenty of delicate knowledge and interfacing with most clients by digital companies. These “advanced” organizations ought to scan over 90% of app releases, consistent with their steady supply of updates and new variations.
App Dev & App Sec Check Frequency
Least Superior: Digital companies are solely a small a part of the enterprise. Only a few app releases annually. Compliance pushed.
Common: Some digital companies, some DevOps, some cloud companies. Could also be present process digital transformation efforts. A portion of digital enterprise is mission-critical and homes delicate knowledge. Some reliance on third celebration knowledge companies.
Most Superior: Core competency in mission-critical digital companies. Excessive-velocity releases, mature DevOps, many digital belongings/companies. Giant quantities of delicate knowledge to guard. Excessive reliance on third celebration knowledge companies.
Benchmark the Proper Variety of Annual App Sec Assessments
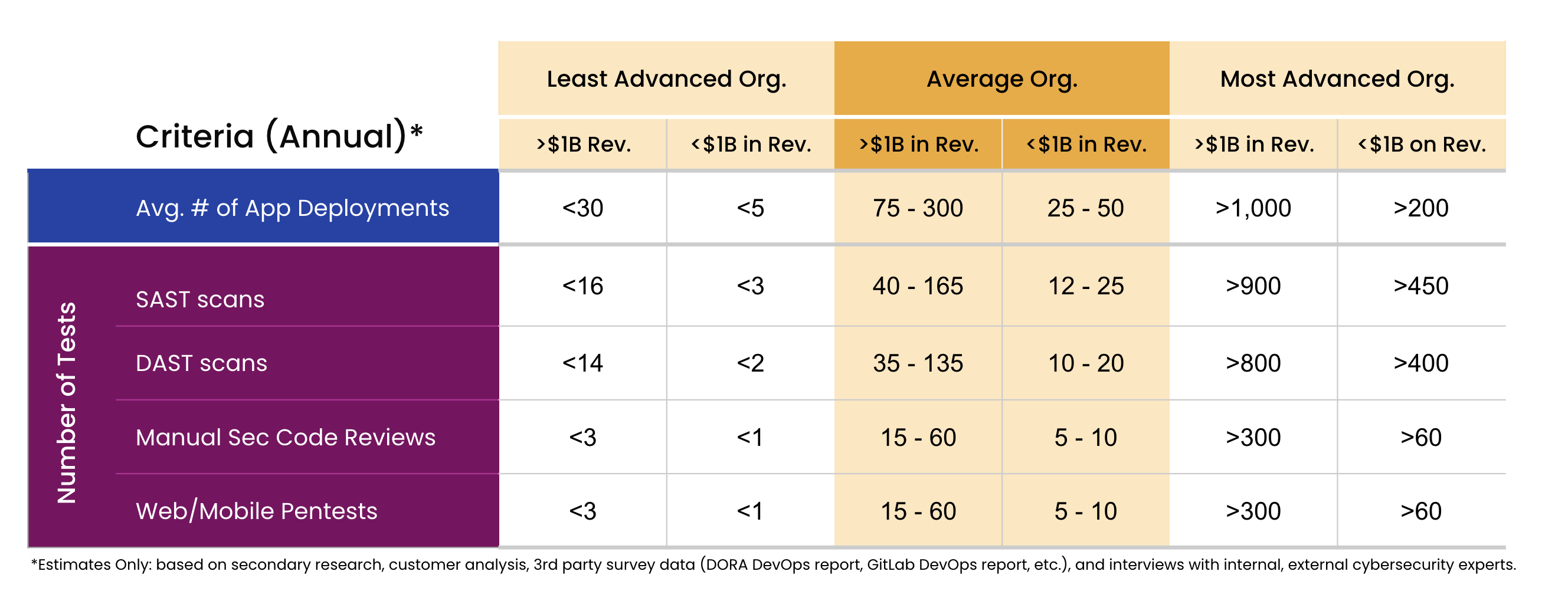
The desk under shows the typical variety of checks a corporation ought to carry out throughout the three ranges of organizational maturity. Really useful testing frequency is proven for each giant enterprises ($1B or extra in income) and SMBs (lower than $1B in income). The scale and scope of every check will differ tremendously between main releases and smaller characteristic updates. Different components of the asset(s) being examined, corresponding to the danger of publicity, knowledge sensitivity, the variety of APIs connecting to third-party companies, the necessity to check underlying infrastructure, microservices, and so on., will even inform the scoping of checks.
A corporation with lower than $1B in annual recurring income beneath the “advanced” SaaS supplier class ought to conduct a minimal of 60 annual pentests. An “average” group of comparable measurement ought to solely conduct between 5 and ten annual pentests. A big “advanced” group with tens of billions in annual income might conceivably conduct over 500 pentests in a given yr.
App Sec Testing Benchmarks
Apply a Systematic Strategy to Optimize your Annual Safety Testing
These benchmarks are a information to assist your group decide the suitable frequency, protection, and the entire variety of safety checks to carry out annually. In case your group’s testing plans are predetermined, use this to validate your assumptions and regulate as wanted.
The scale and scope of every safety check can differ dramatically for main releases in comparison with smaller updates. A big, sophisticated net app could require a 200-hour pentest and an in-depth handbook safety code evaluate, whereas a characteristic replace launch could solely require a 40-hour pentest and single-day code evaluate.
Mix the data included in these tables with what you recognize about your group’s assault floor to reach at a extra correct account of the annual quantity and scope of safety checks which might be proper on your group.
For instance, calculate this for a corporation with lower than $1B in income that does 150 annual app releases. Assume half of those releases are for mission-critical companies, comprise entry to delicate knowledge, and are sure to adjust to the PCI DSS regulation. This places the group within the decrease finish of the <$1B “advanced” group. Given this, fairly assume that:
- ~80% must be SAST scanned
- ~70% must be DAST scanned
- ~25% ought to endure handbook code critiques and pentesting
For the yr, this may lead to:
- 120 SAST scans
- 105 DAST scans
- ~40 handbook code critiques
- ~40 pentests
The HackerOne Evaluation Strategy
Protection-in-depth safety testing makes use of a layered strategy to assist your group check successfully and maximize your restricted sources and funds. Begin with cost-effective and automatic SAST and DAST scans to effectively establish the most typical and well-known vulnerabilities. From there, use human pentesters with the suitable expertise and data to offer context on identified vulnerabilities and establish the extreme vital vulnerabilities generally missed by automated scans. Triage vulnerabilities to prioritize which to repair first, remediate, and use retesting to make sure the fixes work.
These testing approaches complement one another and strengthen general safety posture, serving to your group close its attack resistance gap. Your group ought to at the very least be consistent with the beneficial benchmark averages. Nevertheless, with an ever-expanding assault floor, we advocate a push towards management when evaluating your group’s safety posture towards others of the same measurement and digital maturity.
HackerOne Assessments offers in-depth pentests on a platform designed to simplify remediation on your improvement workforce. Integrations with instruments corresponding to GitHub, Jira, and Slack, enable findings to be delivered instantly into your present workflows. Pentests are one a part of the HackerOne Attack Resistance Management platform, which helps your group clear up safety vulnerabilities from pre-production to deployment. Contact us to learn to obtain assault resistance with HackerOne Assessments.
Author: Spencer Chin
Date: 2022-07-14 12:00:00