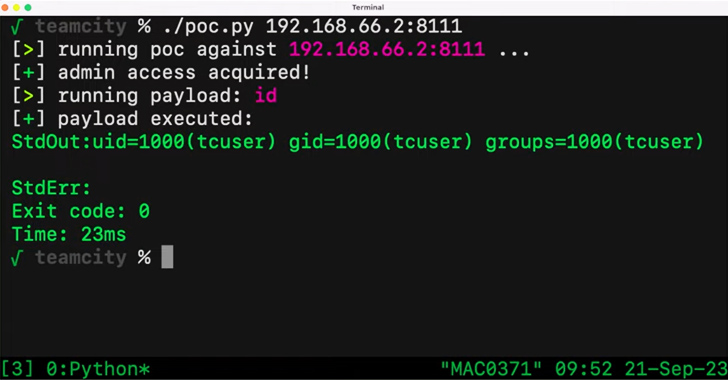
A essential safety vulnerability within the JetBrains TeamCity steady integration and steady deployment (CI/CD) software program may very well be exploited by unauthenticated attackers to realize distant code execution on affected methods.
The flaw, tracked as CVE-2023-42793carries a CVSS rating of 9.8 and has been addressed in TeamCity version 2023.05.4 following accountable disclosure on September 6, 2023.
“Attackers could leverage this access to steal source code, service secrets, and private keys, take control over attached build agents, and poison build artifacts,” Sonar safety researcher Stefan Schiller said in a report final week.

Profitable exploitation of the bug may additionally allow menace actors to entry the construct pipelines and inject arbitrary code, resulting in an integrity breach and provide chain compromises.
Further particulars of the bug have been withheld because of the truth that it is trivial to use, with Sonar noting that it is more likely to be exploited within the wild by menace actors.
JetBrains, in an independent advisoryhas really helpful customers to improve as quickly as potential. It has additionally launched a safety patch plugin for TeamCity variations 8.0 and above to particularly deal with the flaw.
The disclosure comes as two high-severity flaws have been disclosed within the Atos Unify OpenScape merchandise that permit a low-privileged attacker to execute arbitrary working methods instructions as root consumer (CVE-2023-36618) in addition to an unauthenticated attacker to entry and execute numerous configuration scripts (CVE-2023-36619).
Fight AI with AI — Battling Cyber Threats with Next-Gen AI Tools
Able to deal with new AI-driven cybersecurity challenges? Be a part of our insightful webinar with Zscaler to deal with the rising menace of generative AI in cybersecurity.
The issues had been patched by Atos in July 2023.
Over the previous few weeks, Sonar has additionally printed particulars about essential cross-site scripting (XSS) vulnerabilities affecting encrypted e mail options, together with Proton Mail, Skiffand Tutanotathat would have been weaponized to steal emails and impersonate victims.
Author: information@thehackernews.com (The Hacker Information)
Date: 2023-09-26 01:00:00