A financially motivated menace actor has been outed as an preliminary entry dealer (IAB) that sells entry to compromised organizations for different adversaries to conduct follow-on assaults similar to ransomware.
SecureWorks Counter Menace Unit (CTU) has dubbed the e-crime group Gold Melodywhich can be recognized by the names Prophet Spider (CrowdStrike) and UNC961 (Mandiant).
“This financially motivated group has been active since at least 2017, compromising organizations by exploiting vulnerabilities in unpatched internet-facing servers,” the cybersecurity firm said.
“The victimology suggests opportunistic attacks for financial gain rather than a targeted campaign conducted by a state-sponsored threat group for espionage, destruction, or disruption.”

Gold Melody has been previously linked to attacks exploiting safety flaws in JBoss Messaging (CVE-2017-7504), Citrix ADC (CVE-2019-19781), Oracle WebLogic (CVE-2020-14750 and CVE-2020-14882), GitLab (CVE-2021-22205), Citrix ShareFile Storage Zones Controller (CVE-2021-22941), Atlassian Confluence (CVE-2021-26084), ForgeRock AM (CVE-2021-35464), and Apache Log4j (CVE-2021-44228) servers.
The cybercrime group has been noticed increasing its victimology footprint to strike retail, well being care, vitality, monetary transactions, and high-tech organizations in North America, Northern Europe, and Western Asia as of mid-2020.
Mandiant, in an evaluation printed in March 2023, stated that “in multiple instances, UNC961 intrusion activity has preceded the deployment of Maze and Egregor ransomware from distinct follow-on actors.”
It additional described the group as “resourceful in their opportunistic angle to initial access operations” and famous it “employs a cost-effective approach to achieve initial access by exploiting recently disclosed vulnerabilities using publicly available exploit code.”
In addition to counting on a various arsenal comprising net shells, built-in working system software program, and publicly accessible utilities, it is recognized to make use of proprietary distant entry trojans (RATs) and tunneling instruments similar to GOTROJ (aka MUTEPUT), BARNWORK, HOLEDOOR, DARKDOOR, AUDITUNNEL, HOLEPUNCH, LIGHTBUNNY, and HOLERUN to execute arbitrary instructions, collect system info, and set up a reverse tunnel with a hard-coded IP handle.
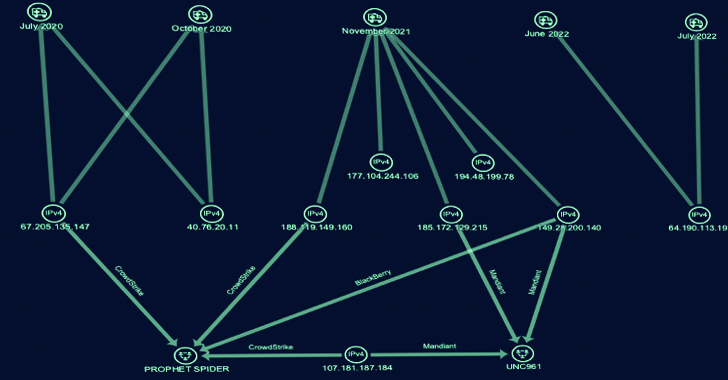
Secureworks, which linked Gold Melody to 5 intrusions between July 2020 and July 2022, stated these assaults entailed the abuse of a special set of flaws, together with these impacting Oracle E-Enterprise Suite (CVE-2016-0545), Apache Struts (CVE-2017-5638), Sitecore XP (CVE-2021-42237), and Flexera FlexNet (CVE-2021-4104) to acquire preliminary entry.
AI vs. AI: Harnessing AI Defenses Against AI-Powered Risks
Able to sort out new AI-driven cybersecurity challenges? Be part of our insightful webinar with Zscaler to handle the rising menace of generative AI in cybersecurity.
A profitable foothold is succeeded by the deployment of net shells for persistence, adopted by creating directories within the compromised host to stage the instruments used within the an infection chain.
“Gold Melody conducts a considerable amount of scanning to understand a victim’s environment,” the corporate stated. “Scanning begins shortly after gaining access but is repeated and continued throughout the intrusion.”
The reconnaissance part paves the way in which for credential harvesting, lateral motion, and knowledge exfiltration. That stated, all 5 assaults finally proved to be unsuccessful.
“Gold Melody acts as a financially motivated IAB, selling access to other threat actors,” the corporate concluded. “The buyers subsequently monetize the access, likely through extortion via ransomware deployment.”
“Its reliance on exploiting vulnerabilities in unpatched internet-facing servers for access reinforces the importance of robust patch management.”
Author: data@thehackernews.com (The Hacker Information)
Date: 2023-09-21 05:11:00