SOC 2, ISO, HIPAA, Cyber Necessities – all the safety frameworks and certifications at the moment are an acronym soup that may make even a compliance professional’s head spin. Should you’re embarking in your compliance journey, learn on to find the variations between requirements, which is finest for your enterprise, and the way vulnerability administration can support compliance.
What’s cybersecurity compliance?
Cybersecurity compliance means you will have met a set of agreed guidelines concerning the best way you defend delicate info and buyer information. These guidelines will be set by legislation, regulatory authorities, commerce associations or business teams.
For instance, the GDPR is about by the EU with a variety of cybersecurity necessities that each group inside its scope should adjust to, whereas ISO 27001 is a voluntary (however internationally acknowledged) set of finest practices for info safety administration. Clients more and more anticipate the reassurance that compliance brings, as a result of breaches and information disclosure will impression their operations, income and repute too.
Which cybersecurity compliance customary is best for you?
Each enterprise in each business is operationally totally different and has totally different cybersecurity wants. The safeguards used to maintain hospital affected person data confidential will not be the identical because the laws for protecting prospects’ monetary info safe.
For sure industries, compliance is the legislation. Industries that cope with delicate private info reminiscent of healthcare and finance are extremely regulated. In some instances, cybersecurity laws overlap throughout industries. For instance, when you’re a enterprise within the EU that handles bank card funds, you then’ll should be compliant with each credit score and banking card laws (PCI DSS) and GDPR.
Safety fundamentals like threat assessments, encrypted information storage, vulnerability administration and incident response plans are pretty widespread throughout requirements, however what techniques and operations should be secured, and the way, are particular to every customary. The requirements we discover beneath are removed from exhaustive, however they’re the most typical compliance for start-ups and SaaS companies that deal with digital information. Let’s dive in.
GDPR
The Basic Knowledge Safety Regulation (GDPR) is a far-reaching piece of laws that governs how companies – together with these within the US – accumulate and retailer the non-public information of European Union residents. Fines for non-compliance are excessive and the EU is not shy about enforcing them.
Who must adjust to GDPR?
Buckle up as a result of it is anybody that collects or processes the private information of anybody within the EU, wherever they go or store on-line. Private info or “personal data” consists of absolutely anything from the title and date of delivery to geographic info, IP handle, cookie identifiers, well being information and fee info. So, when you do enterprise with EU residents, you are required to adjust to GDPR.
How vulnerability scanning can support compliance with GDPR
Your IT safety coverage for GDPR would not need to be an advanced doc – it simply wants to put out in easy-to-understand phrases, the safety protocols your enterprise and workers ought to observe. You can even use free templates from SANS as fashions.
You can begin taking easy steps straight away. There are automated platforms that make it simpler to work out which necessities you already meet, and which of them it is advisable appropriate. For instance, you are required to “develop and implement appropriate safeguards to restrict or include the impression of a possible cybersecurity occasion” which vulnerability scanning utilizing a instrument like Intruder will help you obtain.
SOC 2
SaaS and born-in-the-cloud companies that present digital providers and techniques will probably be most aware of SOC 2 because it covers the storage, dealing with and transmission of digital information, though certification is turning into more and more well-liked with all service suppliers.
There are two stories: Kind 1 is a point-in-time evaluation of your cyber safety posture; Kind 2 is an ongoing audit by an exterior assessor to verify you are assembly these commitments, reviewed and renewed each 12 months. SOC 2 provides you some wiggle room on find out how to meet its standards, whereas PCI DSS, HIPAA and different safety frameworks have very specific necessities.
Who wants SOC 2 compliance?
Whereas SOC 2 is not a authorized requirement, it is essentially the most sought-after safety framework for rising SaaS suppliers. It is faster and cheaper to realize than a lot of the different requirements on this record, whereas nonetheless demonstrating a concrete dedication to cyber safety.
How do you adjust to SOC 2?
SOC 2 compliance requires you to place in place controls or safeguards on system monitoring, information alert breaches, audit procedures and digital forensics. The following SOC 2 report is the auditor’s opinion on how these controls match the necessities of 5 ‘belief ideas’: safety, confidentiality, processing integrity, availability and privateness.
ISO 27001
ISO produces a set of voluntary requirements for quite a lot of industries – ISO 27001 is the standard for best practice in an ISMS (info safety administration system) to handle the safety of economic info, mental property, personnel info, and different third-party info. ISO 27001 just isn’t a authorized requirement by default, however many massive enterprises or authorities businesses will solely work with you when you’re ISO licensed. It is recognised as one of the crucial rigorous frameworks but it surely’s notoriously tough, costly and time consuming to finish.
Who wants it?
Like SOC 2, ISO 27001 is an effective approach to show publicly that your enterprise is dedicated and diligent in terms of info safety, and that you have taken steps to maintain the information you share with them safe.
How do you adjust to ISO 27001?
Third-party auditors validate that you have applied all the related finest practices in accordance with the ISO customary. There is not a common ISO 27001 guidelines that ensures certification. It is as much as you to resolve find out how to resolve what’s in scope and implement the framework, and auditors will use their discretion to judge every case.
Do not forget that ISO 27001 is basically about threat administration. Dangers will not be static and evolve as new cyber threats emerge, so you must construct automated vulnerability management with a instrument like Intruder into your safety controls to judge and analyze new dangers as they emerge. Automated compliance platforms reminiscent of Drata will help pace up the method.
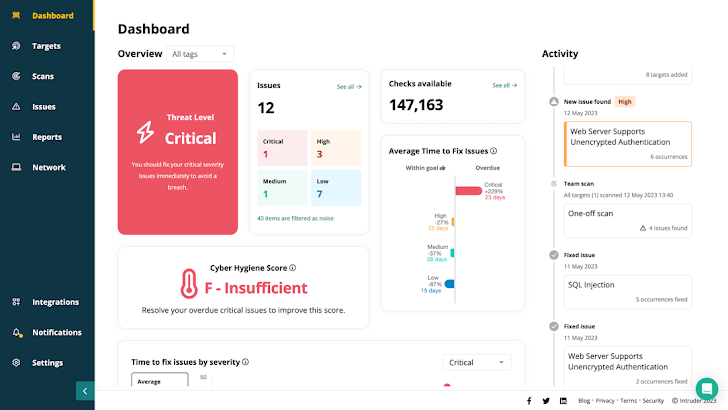 |
| Intruder supplies actionable, audit prepared stories, so you’ll be able to simply present your safety posture to auditors, stakeholders and prospects |
PCI DSS
The PCI DSS (Knowledge Safety Commonplace) was developed by the PCI Safety Requirements Council and the foremost card manufacturers (American Specific, Mastercard and Visa) to manage anybody that shops, processes, and/or transmits cardholder information.
Who wants it?
In principle, anybody that processes card fee transactions, however there are totally different guidelines relying on the quantity and kind of funds you’re taking. Should you use a third-party card fee supplier like Stripe or Sage, they need to handle the method and supply validation for you.
Tips on how to adjust to PCI DSS
In contrast to ISO 27001 and SOC 2, PCI DSS requires a strict vulnerability administration program however accreditation is complicated. Third-party fee suppliers will often populate the PCI kind robotically, offering validation on the click on of a button. For smaller companies, this may save hours of labor.
HIPAA
HIPAA (the Well being Insurance coverage Portability and Accountability Act) regulates the switch and storage of affected person information within the US healthcare business, the place compliance is a authorized requirement.
Who wants it?
HIPAA compliance is necessary for any enterprise that handles affected person info within the US, or anybody doing enterprise within the US with firms which are additionally HIPAA compliant.
Tips on how to adjust to HIPAA
HIPAA will be tough to navigate. It requires a threat administration plan with safety measures ample to cut back threat to an affordable and acceptable stage. Though HIPAA would not specify the methodology, vulnerability scans or penetration checks with a instrument like Intruder ought to be integral parts of any threat evaluation and administration course of.
Cyber Necessities
Cyber Necessities is a UK government-backed scheme designed to verify companies are adequately protected in opposition to widespread cyberattacks. Just like SOC 2, consider it pretty much as good cyber hygiene – like washing your arms or brushing your tooth. Designed for the smaller enterprise with out devoted safety experience, it ought to be simply the place to begin of a extra strong safety program
Who wants Cyber Necessities compliance?
Any enterprise bidding for a UK authorities or public sector contract which includes delicate and private info or offering sure technical services and products.
Tips on how to adjust to Cyber Necessities
The fundamental certificates is a self-assessment of primary safety controls. Cyber Necessities Plus is a extra superior, complete, hands-on technical certification that features a sequence of vulnerability checks that may be supplied by an automatic instrument like Intruder. The inner take a look at is an authenticated inside scan and a take a look at of the safety and anti-malware configuration of every machine.
Compliance would not need to imply complexity
Compliance can appear to be a labour-intensive and costly train, however it might probably pale compared to the price of fixing a breach, paying settlements to prospects, shedding your repute, or paying fines. You can even miss out on potential enterprise if you do not have the certifications prospects anticipate.
However cybersecurity compliance would not should be tough with at the moment’s automated instruments. Should you use Intruder’s vulnerability administration that already integrates with automated compliance platforms like Drata then auditing, reporting and documentation for compliance turns into a complete lot faster and simpler. Whether or not you are simply beginning your compliance journey or seeking to enhance your safety, Intruder will help you get there quicker. Get began at the moment with a free trial.
Author: information@thehackernews.com (The Hacker Information)
Date: 2023-09-26 07:50:00