Tibetan, Uyghur, and Taiwanese people and organizations are the targets of a persistent marketing campaign orchestrated by a risk actor codenamed EvilBamboo to assemble delicate data.
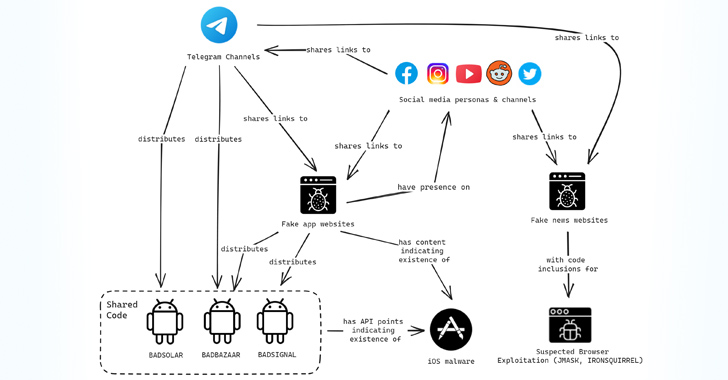
“The attacker has created fake Tibetan websites, along with social media profiles, likely used to deploy browser-based exploits against targeted users,” Volexity safety researchers Callum Roxan, Paul Rascagneres, and Thomas Lancaster mentioned in a report revealed final week.
“Partly through impersonating existing popular communities, the attacker has built communities on online platforms, such as Telegram, to aid in distribution of their malware.”
EvilBamboo, previously tracked by the cybersecurity agency beneath the identify Evil Eye, has been linked to a number of assault waves since at least 2019with the risk actor leveraging watering gap assaults to ship spy ware focusing on Android and iOS gadgets. It is also referred to as Earth Empusa and POISON CARP.

The intrusions directed towards the Apple cellular working system leveraged a then-zero-day vulnerability within the WebKit browser engine that was patched by Apple in early 2019 to ship a spy ware pressure referred to as Insomnia. Meta, in March 2021, mentioned it detected the risk actor abusing its platforms to distribute malicious web sites internet hosting the malware.
The group can also be identified to make use of Android malware akin to ActionSpy and PluginPhantom to reap invaluable knowledge from compromised gadgets beneath the guise of dictionary, keyboard, and prayer apps made accessible on third-party app shops.
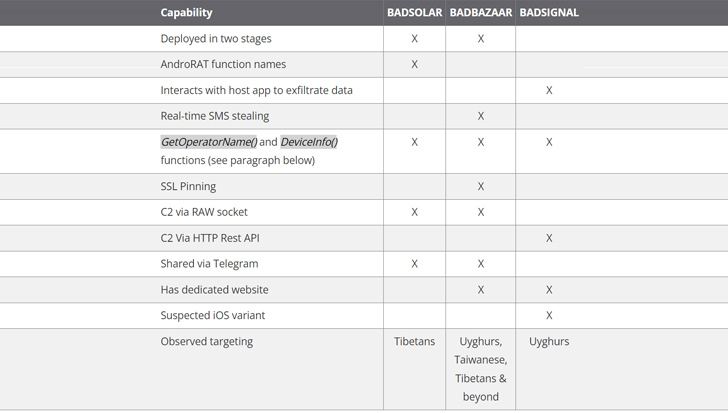
The newest findings from Volexity attribute to EvilBamboo three new Android espionage instruments, specifically BADBAZAAR, BADSIGNAL, and BADSOLAR, the primary of which was documented by Lookout in November 2022.
A subsequent report from ESET final month detailed two trojanized apps masquerading as Sign and Telegram on the Google Play Retailer to entice customers into putting in BADSIGNAL. Whereas the Slovak cybersecurity agency assigned the bogus to the BADBAZAAR household, citing code similarities, Volexity mentioned, “they also appear to be divergent in their development and functionality.”
Assault chains used to distribute the malware households entail using APK sharing boards, pretend web sites promoting Sign, Telegram, and WhatsApp, Telegram channels dedicated to sharing Android apps, and a set of bogus profiles on Fb, Instagram, Reddit, X (previously Twitter), and YouTube.
“The Telegram variants implement the same API endpoints as the Signal variants to gather information from the device and they implement a proxy,” the researchers mentioned, including it recognized endpoints indicating the existence of an iOS model of BADSIGNAL.
One of many Telegram channels can also be mentioned to have contained a hyperlink to an iOS utility named TibetOne that is not accessible within the Apple App Retailer.
Fight AI with AI — Battling Cyber Threats with Next-Gen AI Tools
Able to deal with new AI-driven cybersecurity challenges? Be a part of our insightful webinar with Zscaler to deal with the rising risk of generative AI in cybersecurity.
Messages shared by way of the Telegram teams have additionally been used to distribute functions backdoored with the BADSOLAR malware in addition to booby-trapped hyperlinks that, when visited, run malicious JavaScript to profile and fingerprint the system.
Whereas BADBAZAAR is especially used to focus on Uyghur and different people of the Muslim religion, BADSOLAR seems for use primarily with apps which might be Tibetan-themed. Nonetheless, each strains incorporate their malicious capabilities within the type of a second stage that is retrieved from a distant server.
BADSOLAR’s second-stage malware can also be a fork of an open-source Android distant entry trojan referred to as AndroRAT. BADSIGNAL, in distinction, packs all of its information-gathering features in the principle package deal itself.
“These campaigns largely rely on users installing backdoored apps, which highlights both the importance of only installing apps from trusted authors and the lack of effective security mechanisms to stop backdoored apps making their way on to official app stores,” the researchers mentioned.
“EvilBamboo’s creation of fake websites, and the personas tailored to the specific groups they target, has been a key aspect of their operations, enabling them to build trusted communities that provide further avenues to target individuals with their spyware or for other exploitation.”
Author: information@thehackernews.com (The Hacker Information)
Date: 2023-09-25 06:34:00