Risk actors are leveraging bogus Fb job commercials as a lure to trick potential targets into putting in a brand new Home windows-based stealer malware codenamed Ov3r_Stealer.
“This malware is designed to steal credentials and crypto wallets and send those to a Telegram channel that the threat actor monitors,” Trustwave SpiderLabs said in a report shared with The Hacker Information.
Ov3r_Stealer is able to siphoning IP address-based location, {hardware} information, passwords, cookies, bank card info, auto-fills, browser extensions, crypto wallets, Microsoft Workplace paperwork, and an inventory of antivirus merchandise put in on the compromised host.
Whereas the precise finish purpose of the marketing campaign is unknown, it is seemingly that the stolen info is obtainable on the market to different menace actors. One other chance is that Ov3r_Stealer might be up to date over time to behave as a QakBot-like loader for added payloads, together with ransomware.
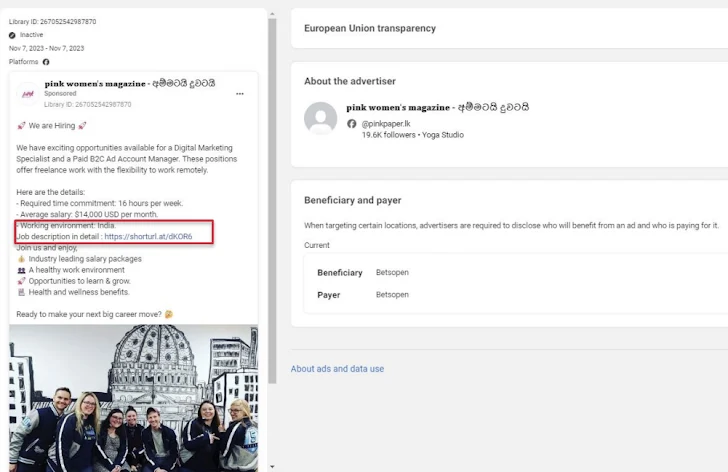
The place to begin of the assault is a weaponized PDF file that purports to be a file hosted on OneDrive, urging customers to click on on an “Access Document” button embedded into it.
Trustwave stated it recognized the PDF file being shared on a pretend Fb account impersonating Amazon CEO Andy Jassy in addition to through Fb adverts for digital promoting jobs.
Customers who find yourself clicking on the button are served an web shortcut (.URL) file that masquerades as a DocuSign doc hosted on Discord’s content delivery network (CDN). The shortcut file then acts as a conduit to ship a management panel merchandise (.CPL) file, which is then executed utilizing the Home windows Management Panel course of binary (“control.exe“).
The execution of the CPL file results in the retrieval of a PowerShell loader (“DATA1.txt”) from a GitHub repository to in the end launch Ov3r_Stealer.
It is price noting at this stage {that a} near-identical infection chain was lately disclosed by Pattern Micro as having put to make use of by menace actors to drop one other stealer known as Phemedrone Stealer by exploiting the Microsoft Home windows Defender SmartScreen bypass flaw (CVE-2023-36025CVSS rating: 8.8).
The similarities prolong to the GitHub repository used (nateeintanan2527) and the truth that Ov3r_Stealer shares code-level overlaps with Phemedrone.
“This malware has recently been reported, and it may be that Phemedrone was re-purposed and renamed to Ov3r_Stealer,” Trustwave stated. “The main difference between the two is that Phemedrone is written in C#.”
The findings come as Hudson Rock revealed that menace actors are promoting their entry to legislation enforcement request portals of main organizations like Binance, Google, Meta, and TikTok by exploiting credentials obtained from infostealer infections.
Additionally they observe the emergence of a class of infections known as CrackedCantil that take leverage cracked software program as an preliminary entry vector to drop loaders like PrivateLoader and SmokeLoader, when subsequently act as a supply mechanism for info stealers, crypto miners, proxy botnets, and ransomware.
Author: information@thehackernews.com (The Hacker Information)
Date: 2024-02-06 09:09:00