What’s Asset Stock?
The effectiveness of an ASM initiative is set by how effectively the answer data the assault floor and presents the info to the group. A best-in-class ASM program should embody a complete stock of a corporation’s rising assault floor. It also needs to get rid of spreadsheets and handbook processes altogether, however it shouldn’t cease there.
The stock functionality of HackerOne Property permits prospects to create and management risk-ranked, {custom} classes for digital property throughout their group. Over time, it turns into a golden document of worldwide exterior property and related safety testing, whereas accelerating ASM and Vulnerability Administration (VM) outcomes.
HackerOne Property prospects can entry the stock functionality through a unified UI to handle their assault floor and the safety testing scopes. The early customers have seen vital enhancements find unknown internet-facing property of their assault floor and managing the related threat. This features a outstanding +2X enchancment in assault floor visibility and management for purchasers that began their ASM program with HackerOne.
How a Major US Bank Prepared for a Multi-Year Cloud Migration with HackerOne Property
The way it Works
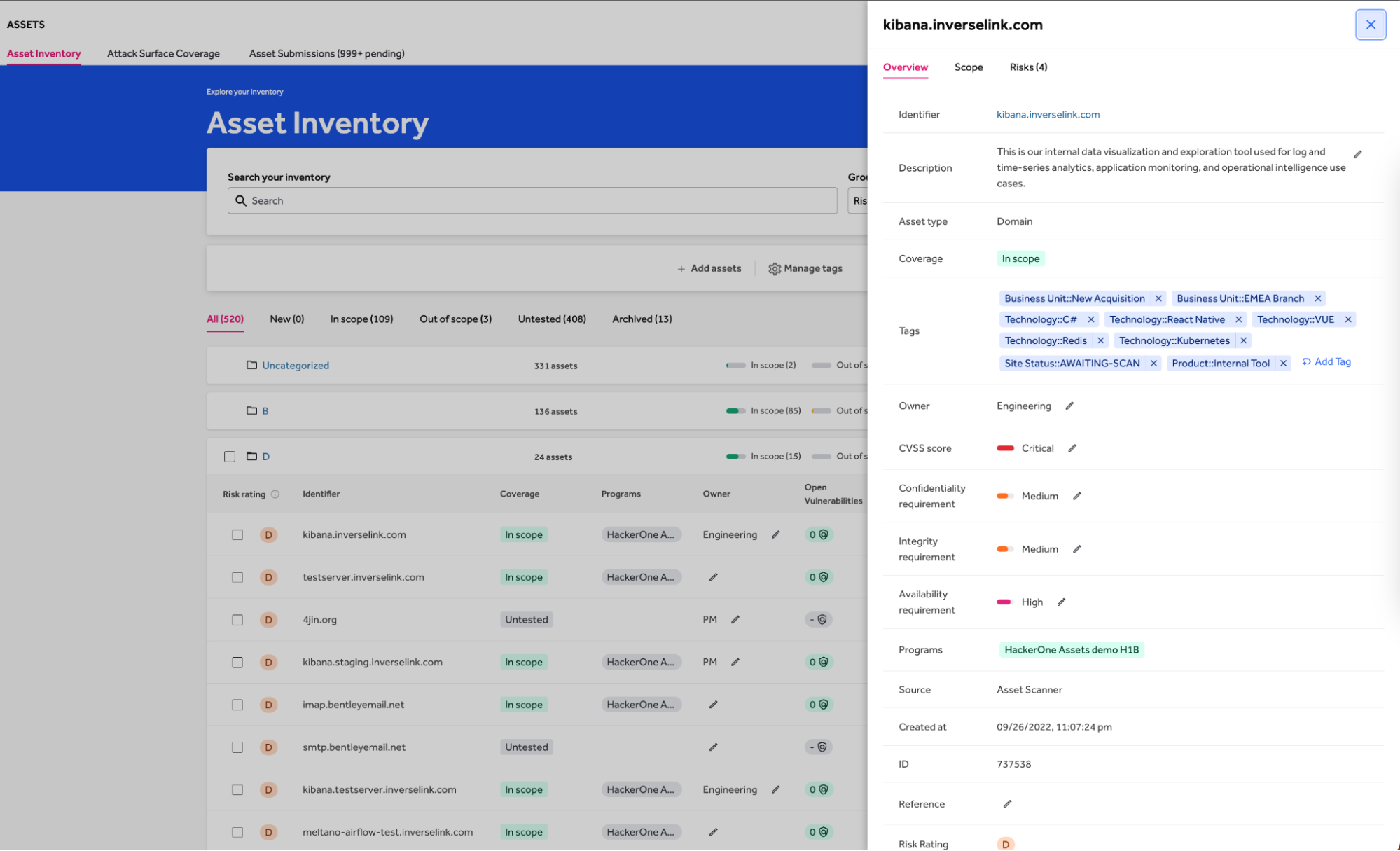
A corporation’s stock exhibits all new property and the property in scope, the protection of their testing packages, and offers a abstract of the open vulnerabilities (Determine 1).
Clicking on a website group on the stock web page opens an in depth checklist of all property beneath that area. From there, asset traits could be edited individually or in bulk. Every asset listed exhibits info on testing protection, program, proprietor, and open vulnerabilities (Determine 1).
The stock can scale from tons of to 1000’s of property effectively and permits {custom} asset tagging. Property tagged with know-how stack, enterprise unit, or geolocation could be additional categorized, filtered, and grouped primarily based on the usual or custom-created tags (Determine 2).
Enriching the Stock With Related Knowledge
In contrast to different ASM options that solely populate the stock with the outcomes of a single scan, the stock characteristic in HackerOne Property ingests outcomes from a number of sources:
- HackerOne’s steady assault floor scanner detects dangerous software program by wanting on the know-how stack and host header..
- Imported information from open-source applied sciences, different ASM options, and homegrown asset administration instruments in CSV format or by the HackerOne API.
- Property found by HackerOne’s group of safety specialists to see vulnerabilities from an adversary’s viewpoint.
E-book your free attack surface reviewand get an actionable threat snapshot in 60 minutes.
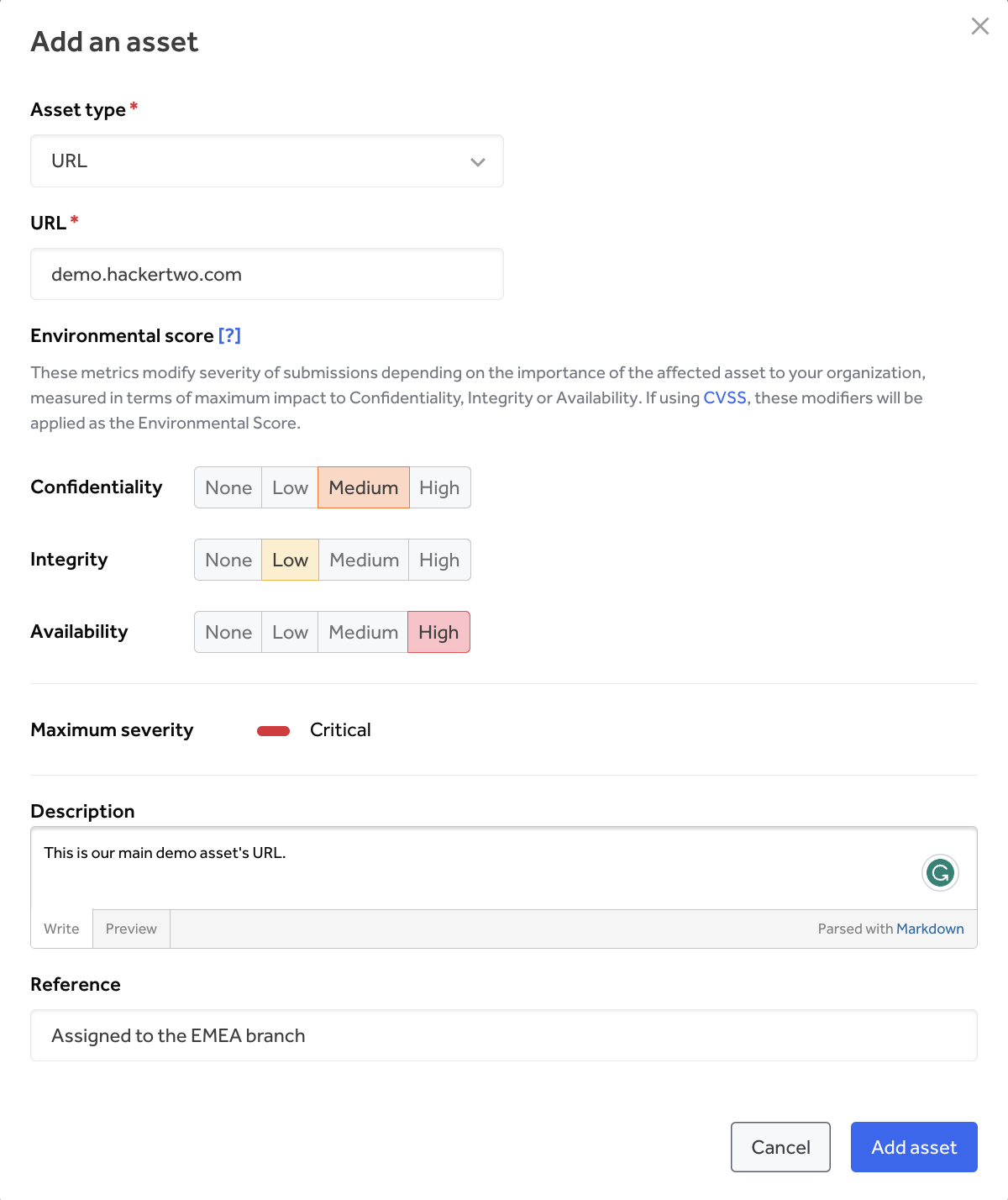
Extra property could be included from the stock web page by clicking ‘Add an asset’ beneath the ‘search & filter’ field. A pop-up menu will seem, prompting customers to enter asset particulars (Determine 3).
Exporting Asset Knowledge to CSV
The CSV Export characteristic permits you to export particulars associated to your property, together with DNS/whois and IP info (Determine 4). It offers all of the important asset metadata in a typical export format, making it simple to share information together with your staff and enhancing safety efficacy throughout your group.
The CSV Export is context-aware and respects the filters and search queries you will have utilized to the stock. This ensures that you just solely export the related information you want, saving time and streamlining your asset administration course of.

Beginning Safety Testing and Managing Scope From Asset Stock
Whereas ASM and safety testing ought to go hand-in-hand, they’re sometimes disconnected in the actual world. Safety groups want a extra environment friendly approach to feed newly found property into present safety testing workflows. This creates redundancy in scope administration throughout every pentest, bounty program, and supplier their group works with. To cut back risk publicity, inventoried digital property should even be threat ranked and remediated quick.
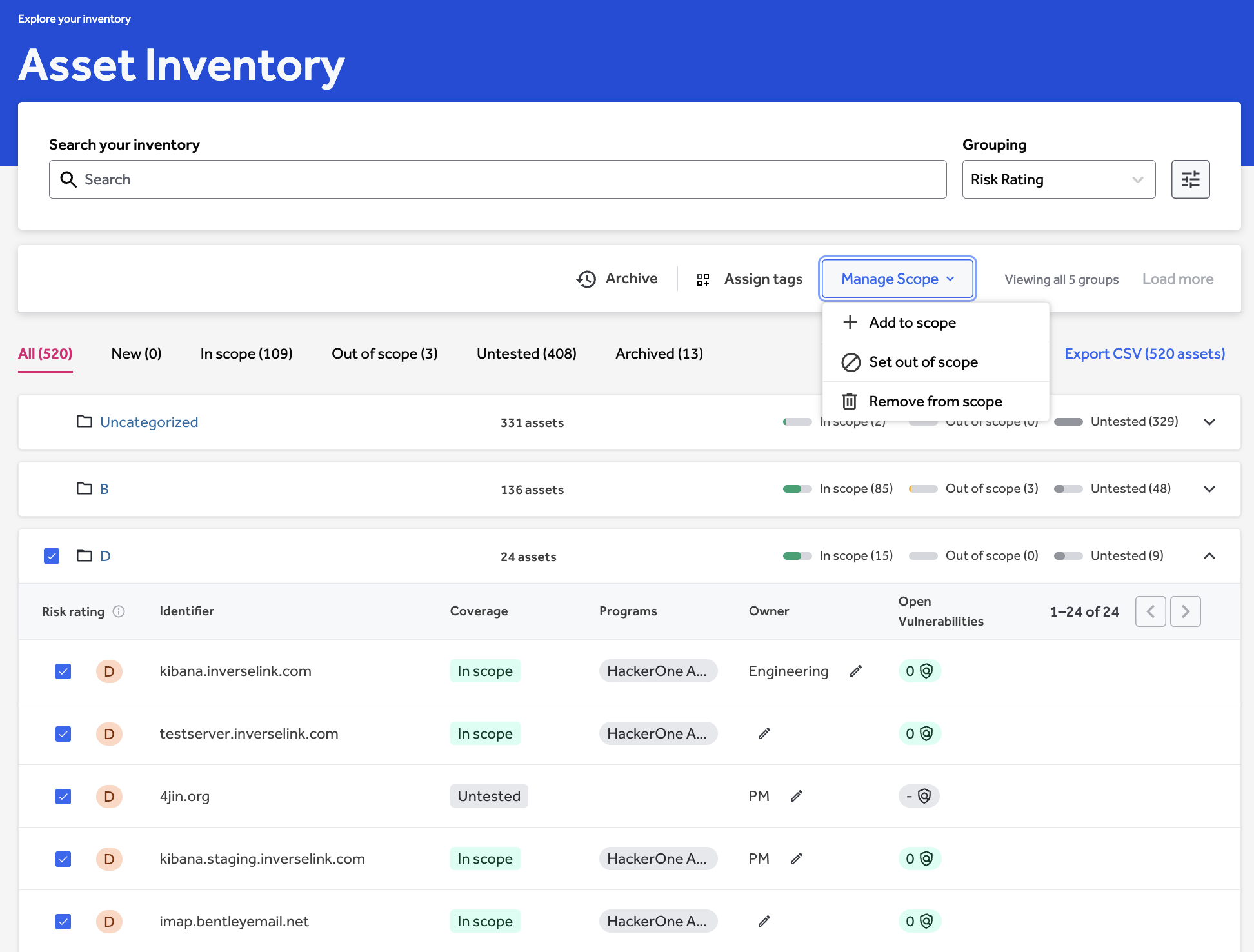
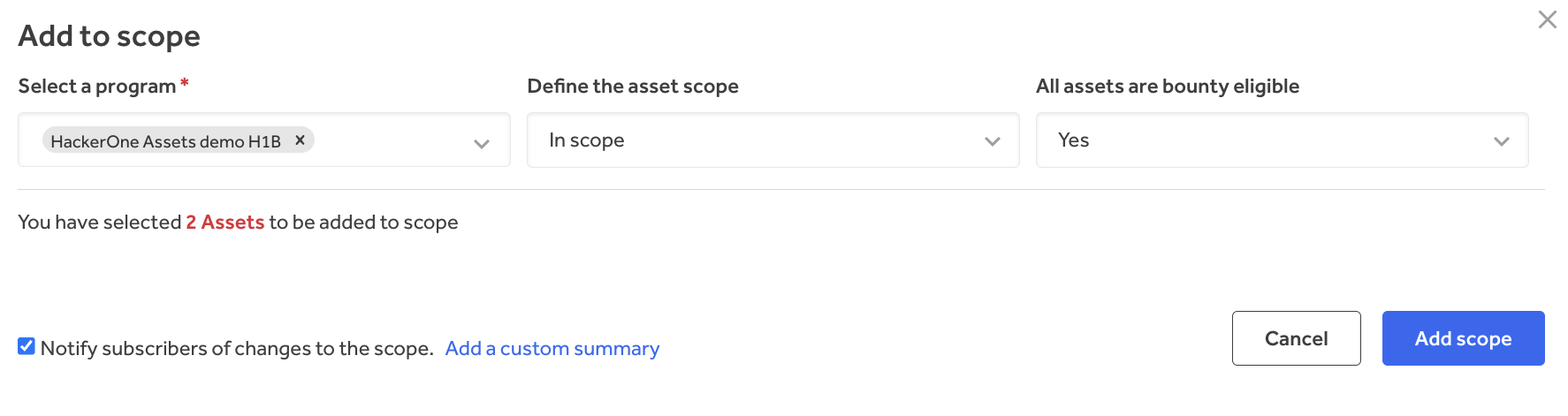
HackerOne addresses this by making it simple for organizations so as to add newly found property on to present adversarial testing scopes inside their stock (Determine 5). A safety staff can full fundamental remediations on a newly found asset, then add it to an lively bug bounty, VDP, or pentest program (Determine 6). This course of ensures that newly recognized dangers are fed into established threat discount processes as a substitute of slipping by the cracks.
Learn extra about Unified HackerOne Scope Management with Burp Suite Support
Scope administration helps the collection of one or a number of property, including them to lively safety checks, and modifying the scope and bounty eligibility through drop-down lists. With enhanced management over the scope, safety groups can work extra effectively by avoiding the duplication of property when overseeing a number of checks.
Curious to be taught extra? Contact us to extend your staff’s capability to guard your assault floor and act on what issues most!
Author: Naz Bozdemir
Date: 2023-03-28 12:00:00



