Indian authorities entities and power corporations have been focused by unknown menace actors with an goal to ship a modified model of an open-source info stealer malware known as HackBrowserData and exfiltrate delicate info in some circumstances by utilizing Slack as command-and-control (C2).
“The information stealer was delivered via a phishing email, masquerading as an invitation letter from the Indian Air Force,” EclecticIQ researcher Arda Büyükkaya said in a report printed at this time.
“The attacker utilized Slack channels as exfiltration points to upload confidential internal documents, private email messages, and cached web browser data after the malware’s execution.”
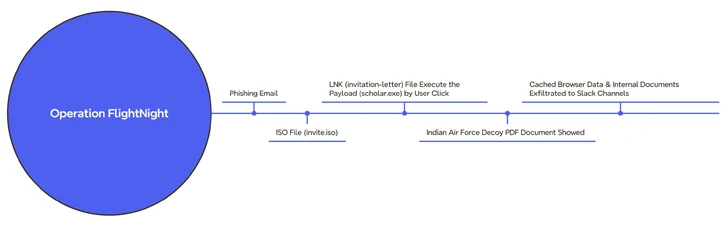
The marketing campaign, noticed by the Dutch cybersecurity agency starting March 7, 2024, has been codenamed Operation FlightNight in reference to the Slack channels operated by the adversary.
Targets of the malicious exercise span a number of authorities entities in India, counting these associated to digital communications, IT governance, and nationwide protection.
The menace actor is alleged to have efficiently compromised personal power corporations, harvesting monetary paperwork, private particulars of workers, particulars about drilling actions in oil and fuel. In all, about 8.81 GB of knowledge has been exfiltrated over the course of the marketing campaign.
The assault chain begins with a phishing message containing an ISO file (“invite.iso”), which, in flip, incorporates a Home windows shortcut (LNK) that triggers the execution of a hidden binary (“scholar.exe”) current inside the mounted optical disk picture.
Concurrently, a lure PDF file that purports to be an invite letter from the Indian Air Power is exhibited to the sufferer whereas the malware clandestinely harvests paperwork and cached internet browser knowledge and transmits them to an actor-controlled Slack channel named FlightNight.
The malware is an altered model of HackBrowserData that goes past its browser knowledge theft options to include capabilities to siphon paperwork (Microsoft Workplace, PDFs, and SQL database recordsdata), talk over Slack, and higher evade detection utilizing obfuscation strategies.
It is suspected that the menace actor stole the decoy PDF throughout a earlier intrusion, with behavioral similarities traced again to a phishing marketing campaign concentrating on the Indian Air Power with a Go-based stealer known as GoStealer.
Particulars of the exercise had been disclosed by an Indian safety researcher who goes by the alias xelemental (@ElementalX2) in mid-January 2024.
The GoStealer an infection sequence is just about similar to that FlightNight, using procurement-themed lures (“SU-30 Aircraft Procurement.iso”) to show a decoy file whereas the stealer payload is deployed to exfiltrate info of curiosity over Slack.
By adapting freely accessible offensive instruments and repurposing official infrastructure akin to Slack that is prevalent in enterprise environments, it permits menace actors to scale back time and growth prices, in addition to simply fly beneath the radar.
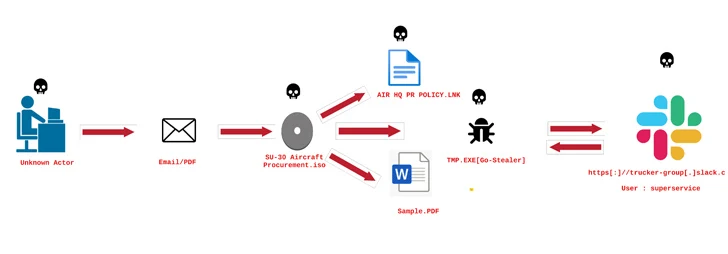 |
| Picture supply: ElementalX2 |
The effectivity advantages additionally imply that it is that a lot simpler to launch a focused assault, even permitting less-skilled and aspiring cybercriminals to spring into motion and inflict vital injury to organizations.
“Operation FlightNight and the GoStealer campaign highlight a simple yet effective approach by threat actors to use open-source tools for cyber espionage,” Büyükkaya stated.
“This underscores the evolving landscape of cyber threats, wherein actors abuse widely used open-source offensive tools and platforms to achieve their objectives with minimal risk of detection and investment.”
Author: data@thehackernews.com (The Hacker Information)
Date: 2024-03-27 11:24:00