This put up will begin with the fundamentals of defining scope and the way moral hackers and testers use it of their testing workflow. For those who’re already acquainted with Burp Suite and the overall thought of scope in software program testing, skip down and begin studying the part that covers Scope Administration.
What’s a scope?
In penetration testing and bug bounty, scope defines the boundaries of an engagement—what is and isn’t to be included in testing. The aim of defining an engagement’s scope is to focus testers’ power on the property, assault vectors, and vulnerability varieties that almost all concern the group. The group operating the engagement defines the scope, often with help from their vendor or bug bounty supplier, to verify it’s correct.
For instance, the aim of an engagement could also be to check a particular, newly-launched software. In that case, the scope would solely embrace that software, with all different property and infrastructure falling out of scope. Alternatively, an engagement may have a far broader scope that features a vary of vital property.
A scope can embrace extra than simply which property are to be examined. Bug bounty scopes, particularly, continuously listing which testing strategies are (and aren’t) allowed and which vulnerability classes the group is (and isn’t) keen to pay out for.
What’s Burp Suite?
Burp Suite—usually referred to easily as Burp—is a set of instruments used to check the safety of net purposes. The suite integrates fundamental instruments, together with:
- Proxy server
- Request repeater
- Scanner
- Spider
- Decoder
- Examine
…with extra superior instruments:
- A Extremely versatile fuzzer
- Sequencer
- A number of extension plugins
- Varied automation capabilities
Collectively these instruments assist all the testing course of—from preliminary mapping and evaluation of an software’s assault floor to discovering and exploiting safety vulnerabilities. Typical Burp Suite customers embrace penetration testers, inner safety groups, and bug bounty hunters.
Defining goal scope in Burp Suite
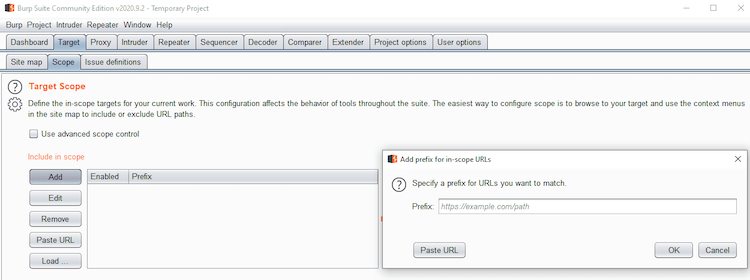
With the scope of an engagement outlined, testers will configure a goal scope inside Burp Suite for every testing undertaking to specify what is going to and won’t be examined. This permits the tester to listing which hosts and URLs can be focused (i.e., attacked) and which can be excluded.
Goal scope in Burp Suite is predicated solely on URLs. A URL will solely be in scope for a undertaking if it matches one thing within the embrace listing and doesn’t match something within the exclude listing.
For instance, a undertaking might embrace the URL:
And exclude the URL:
- https://instance.com/personal
On this case, the scope contains all the things listed below https://instance.com/together with ALL subdirectories—besides the contents of the /personal subdirectory.
Superior controls let you additional outline a undertaking’s scope primarily based on every particular person part of the URL: the protocol, host IP tackle, port numbers, and file path.
Burp Suite permits testers to manually configure a undertaking’s scope and edit it as wanted. Determine 1 above exhibits the best way to add goal URLs to scope in Burp Suite manually. Extra particulars on defining goal scope in Burp Suite might be discovered here.
HackerOne Scope Administration
Usually, there may be a number of redundancy in scope administration throughout every pentest, program, and supplier that your group works with. It may be time intensive for a safety group to manually observe all modifications to their group’s property and mirror them within the scope of a number of checks. As soon as your group has taken the time to set the scope precisely, there isn’t a simple strategy to get that scope immediately into testers’ instruments.
That is the place the HackerOne platform is available in. The brand new Scope Administration function within the HackerOne platform permits clients to simply handle their bug bounty, Vulnerability Disclosure Program, and pentest scopes from a single interface.
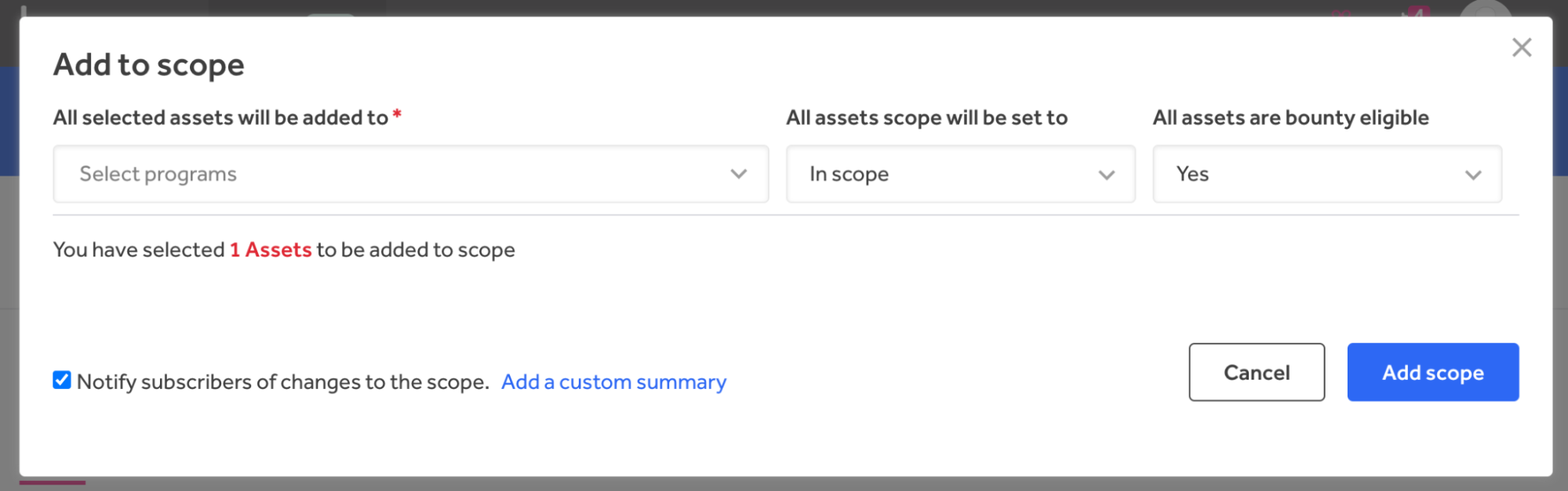
Scope Administration permits safety groups to pick one or a number of property, add them to lively checks, and modify the scope and bounty eligibility by way of drop-down lists, as proven in Determine 2.
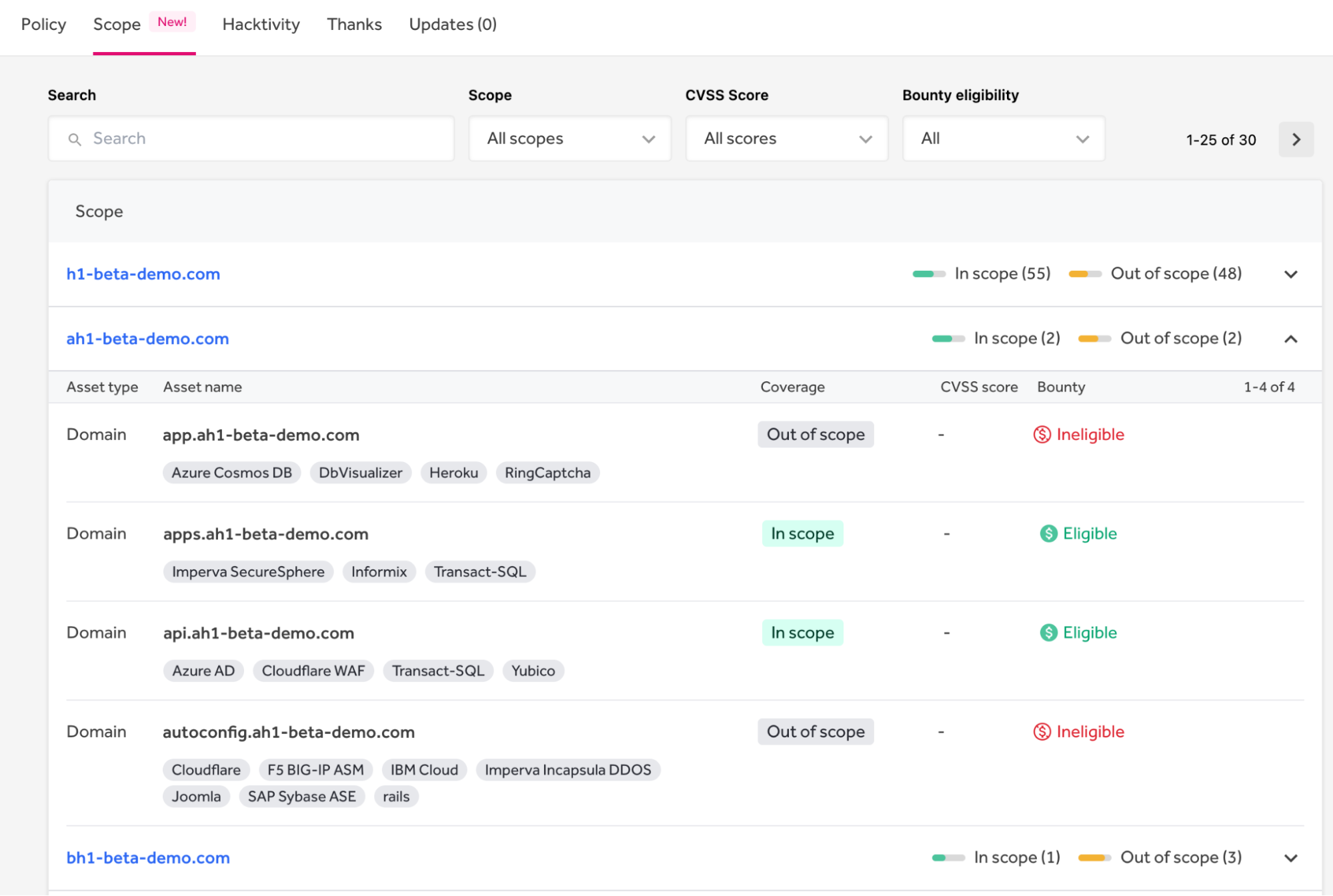
Property are organized into teams below a single area. All property linked to a website might be seen by increasing an asset group. Every asset has a sort (e.g., area, URL, IP Tackle, software, {hardware}, and lots of others), a reputation, protection (in or out of scope), a CVSS rating, and whether or not it’s eligible for bounty. Tags present the expertise stack particulars. For instance, as proven in Determine 3 under, api.ah1-beta-demo.com is in scope, eligible for bounty, and makes use of Azure Energetic Listing, the Cloudflare WAF, and different applied sciences.
Automating the creation and upkeep of scope saves time and avoids errors. With this enhanced management over scope, safety workers can work extra effectively by avoiding the duplication of property when overseeing a number of checks.
Simply Import Scoped Property into Burp Suite
Program pages function a brand new Scope tab the place hackers can view and filter property which can be in or out of scope. This tab will increase the discoverability of property by offering in-platform workflows that allow bounty hunters and pentesters to go looking and filter a buyer’s scope, as seen under in Determine 4. This permits hackers to hone in on the property and dangers they concentrate on, even when your scope contains 1000’s of property.
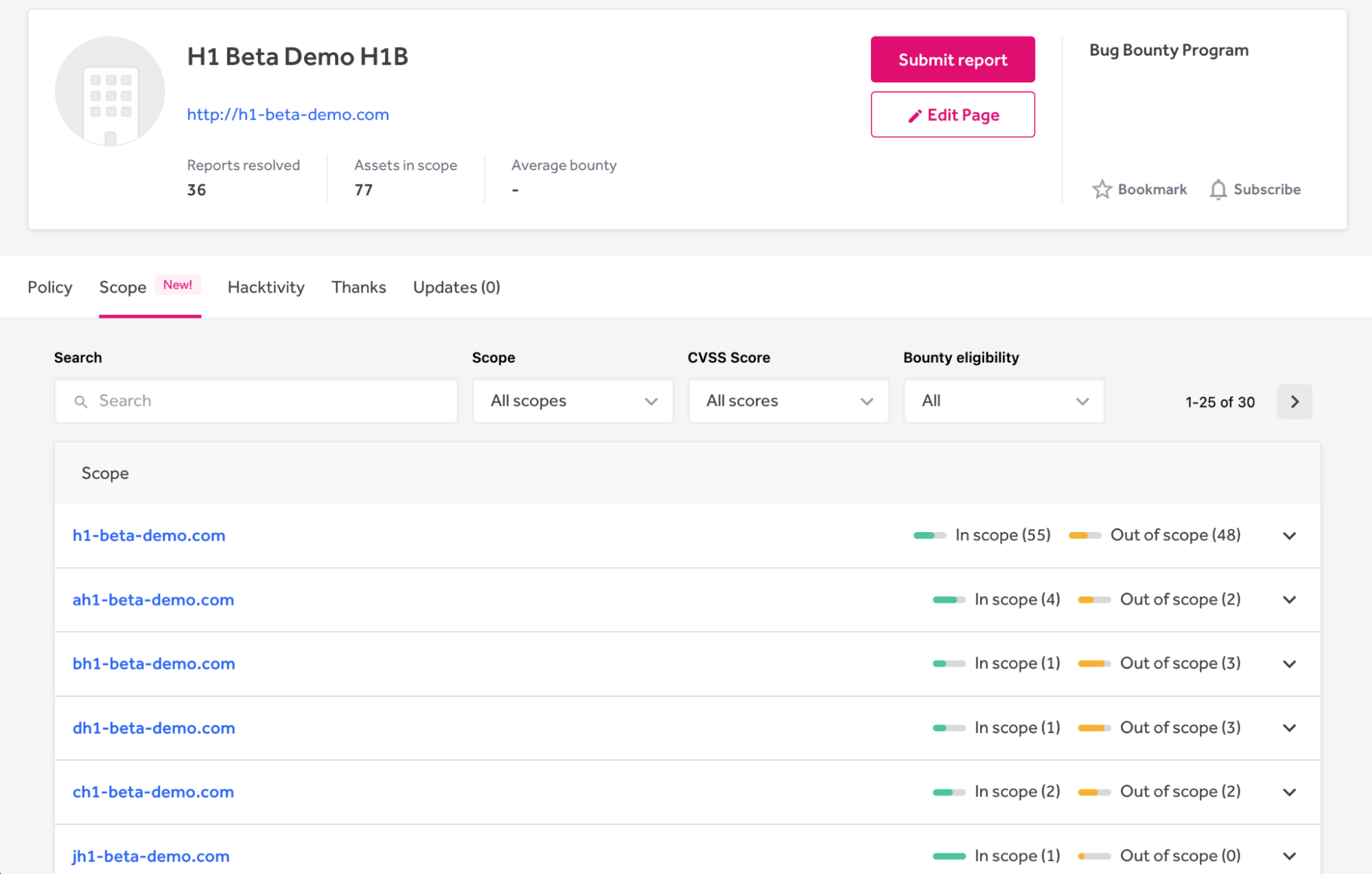
Hackers and testers can filter your scope by CVSS rating and bounty eligibility. Then, they’ll simply import filtered property immediately into BurpSuite with a dynamically generated Burp Suite Mission Configuration file, proven in Determine 5. This file comprises an inventory of URLs for use because the goal scope matching the utilized filters.
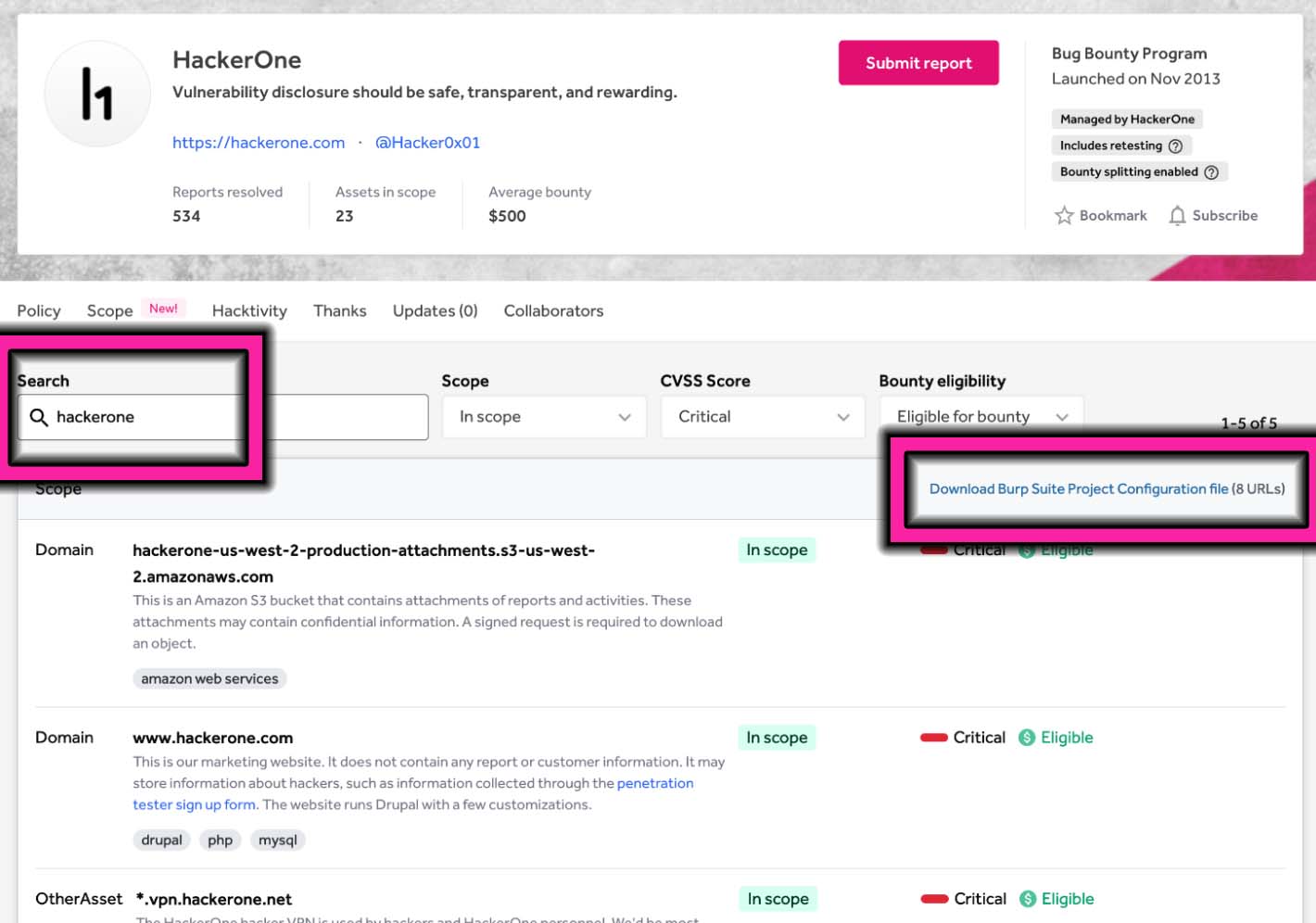
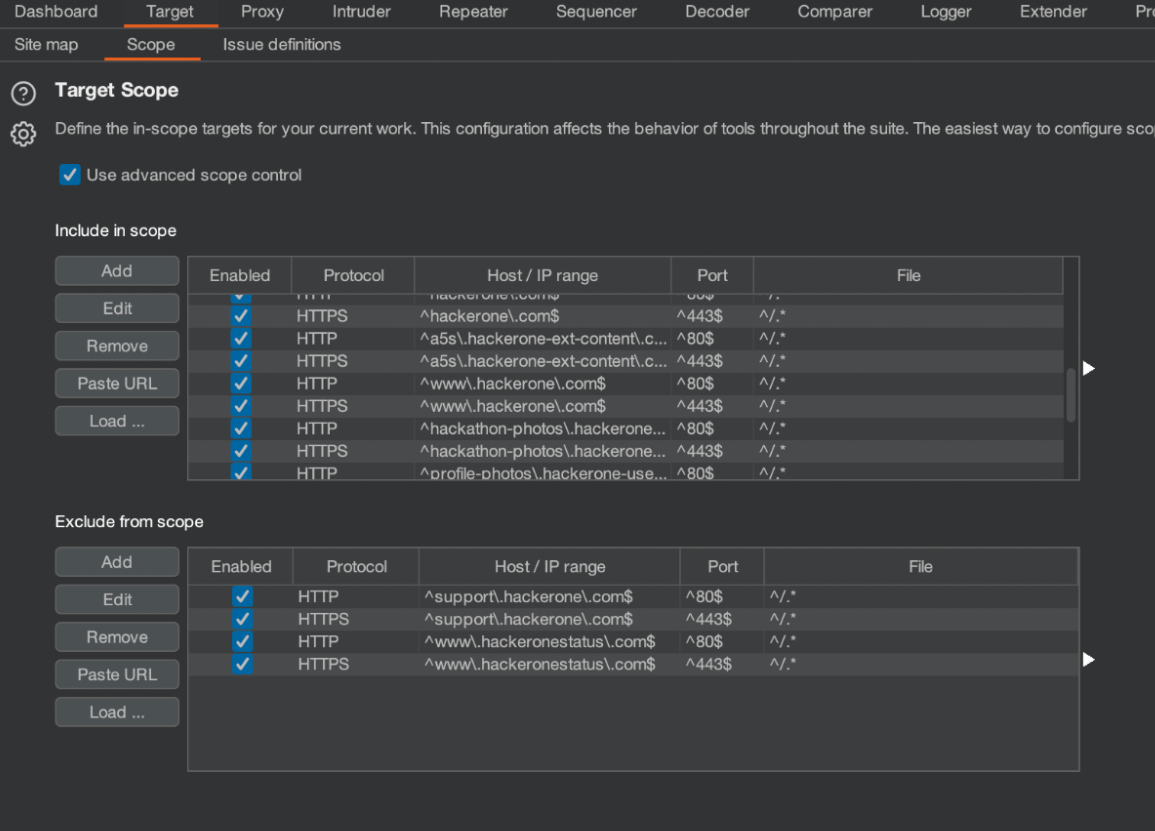
Automating the creation of a Burp Suite Mission Configuration file lets hackers begin testing extra rapidly and removes human error when setting it up manually. Determine 6 exhibits the scope file after it’s imported into BurpSuite. This functionality works in HackerOne Bounty and in HackerOne Property, so pentesters may also benefit from it.
Scope Administration Improves Effectivity and Testing Outcomes
Scope Administration improves your group’s engagements. Safety operations workers save time organising and sustaining scopes for pentests and bug bounty. The brand new Scope tab helps penetration testers and bug bounty hunters discover and perceive property extra simply. Lastly, mechanically up to date Burp Suite configuration recordsdata pace up undertaking setup for pentesters and bounty hunters engaged on packages operating on HackerOne.
Author: Tim Matthews
Date: 2022-09-15 18:00:00