A novel cloud-native cryptojacking operation has set its eyes on unusual Amazon Net Companies (AWS) choices akin to AWS Amplify, AWS Fargate, and Amazon SageMaker to illicitly mine cryptocurrency.
The malicious cyber exercise has been codenamed AMBERSQUID by cloud and container safety agency Sysdig.
“The AMBERSQUID operation was able to exploit cloud services without triggering the AWS requirement for approval of more resources, as would be the case if they only spammed EC2 instances,” Sysdig safety researcher Alessandro Brucato stated in a report shared with The Hacker Information.
“Targeting multiple services also poses additional challenges, like incident response, since it requires finding and killing all miners in each exploited service.”

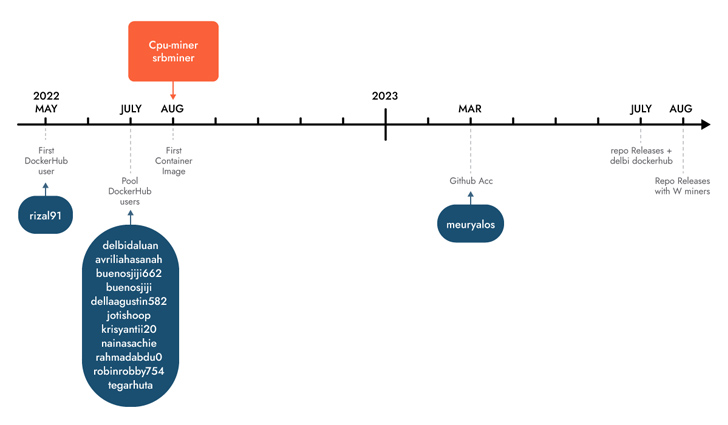
Sysdig stated it found the marketing campaign following an analysis of 1.7 million images on Docker Hub, attributing it with average confidence to Indonesian attackers based mostly on using Indonesian language in scripts and usernames.
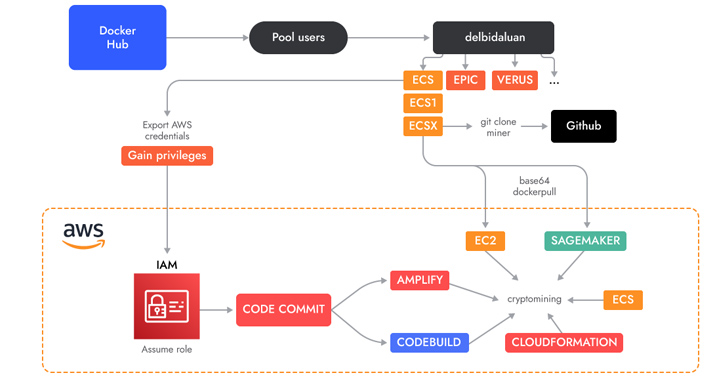
A few of these photos are engineered to execute cryptocurrency miners downloaded from actor-controlled GitHub repositories, whereas others run shell scripts concentrating on AWS.
A key attribute is the abuse of AWS CodeCommit, which is used to host non-public Git repositories, to “generate a private repository which they then used in different services as a source.”
The repository accommodates the supply code of an AWS Amplify app that, in flip, is leveraged by a shell script to create a Amplify internet app and in the end launch the cryptocurrency miner.
The menace actors have additionally been noticed using shell scripts to carry out cryptojacking in AWS Fargate and SageMaker cases, incurring important compute prices for the victims.
Sysdig estimated that AMBERSQUID might lead to losses of greater than $10,000 per day if it is scaled to focus on all AWS regions. An additional evaluation of the pockets addresses used reveals that the attackers have earned greater than $18,300 in revenues so far.
AI vs. AI: Harnessing AI Defenses Against AI-Powered Risks
Able to sort out new AI-driven cybersecurity challenges? Be part of our insightful webinar with Zscaler to handle the rising menace of generative AI in cybersecurity.
This isn’t the primary time Indonesian menace actors have been linked to cryptojacking campaigns. In Might 2023, Permiso P0 Labs detailed an actor named GUI will which was noticed leveraging Amazon Net Companies (AWS) Elastic Compute Cloud (EC2) cases to hold out crypto mining operations.
Michael Clark, director of menace analysis at Sysdig, instructed The Hacker Information that “there doesn’t appear to be much cross-over between the TTPs of the two attacks,” and that they’re more than likely carried out by completely different teams.
“But it does show that Indonesia has a thriving community around cryptojacking,” Clark identified.
“While most financially motivated attackers target compute services, such as EC2, it is important to remember that many other services also provide access to compute resources (albeit it more indirectly),” Brucato stated.
“It is easy for these services to be overlooked from a security perspective since there is less visibility compared to that available through runtime threat detection.”
Author: information@thehackernews.com (The Hacker Information)
Date: 2023-09-18 08:30:00