The peer-to-peer (P2) worm often called P2PInfect has witnessed a surge in exercise since late August 2023, witnessing a 600x soar between September 12 and 19, 2023.
“This increase in P2PInfect traffic has coincided with a growing number of variants seen in the wild, suggesting that the malware’s developers are operating at an extremely high development cadence,” Cado Safety researcher Matt Muir said in a report printed Wednesday.
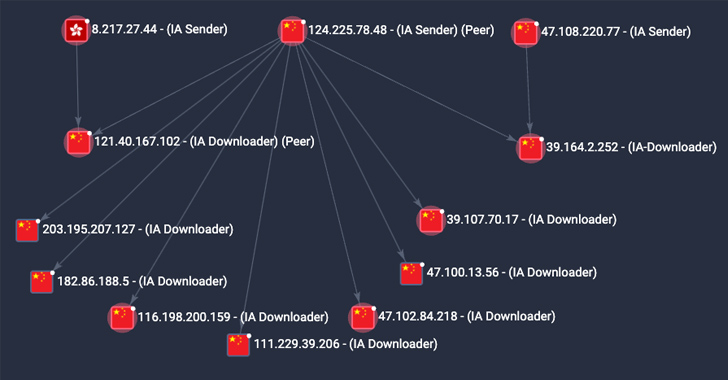
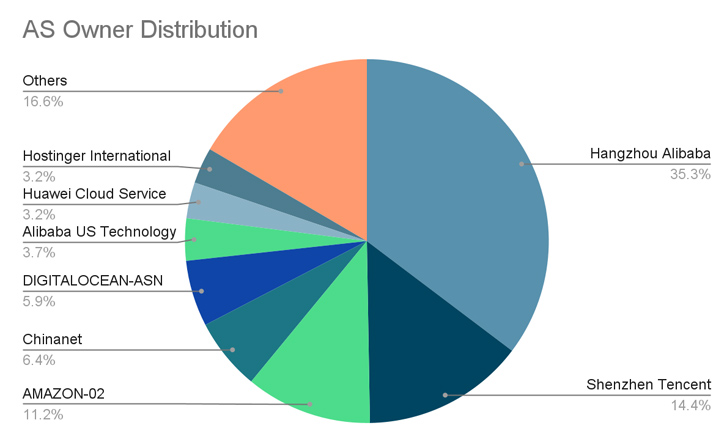
A majority of the compromises have been reported in China, the U.S., Germany, the U.Ok., Singapore, Hong Kong, and Japan.
P2PInfect first got here to mild in July 2023 for its means to breach poorly secured Redis situations. The menace actors behind the marketing campaign have since resorted to totally different approaches for preliminary entry, together with the abuse of the database’s replication function to ship the malware.

Cado Safety mentioned it has noticed a rise in preliminary entry occasions attributable to P2PInfect wherein the Redis SLAVEOF command is issued by an actor-controlled node to a goal to allow replication.
That is adopted by delivering a malicious Redis module to the goal, which, in flip, runs a command to retrieve and launch the principle payload, after which one other shell command is run to take away the Redis module from the disk in addition to disable the replication.
One of many new options of the newer variants is the addition of a persistence mechanism that leverages a cron job to launch the malware each half-hour.Moreover, there now exists a secondary methodology that retrieves a replica of the malware binary from a peer and executes ought to or not it’s deleted or the principle course of is terminated.
P2PInfect additional overwrites current SSH authorized_keys information with an attacker-controlled SSH key, successfully stopping current customers from logging in over SSH.
“The main payload also iterates through all users on the system and attempts to change their user passwords to a string prefixed by Pa_ and followed by 7 alphanumeric characters (e.g. Pa_13HKlak),” Muir mentioned. This step, nonetheless, requires that the malware has root entry.
Level-Up SaaS Security: A Comprehensive Guide to ITDR and SSPM
Keep forward with actionable insights on how ITDR identifies and mitigates threats. Be taught in regards to the indispensable position of SSPM in guaranteeing your id stays unbreachable.
Regardless of the rising sophistication of the malware, P2PInfect’s precise objectives are unclear. Cado Safety mentioned it noticed the malware making an attempt to fetch a crypto miner payload, however there isn’t a proof of cryptomining to this point.
“It’s clear that P2PInfect’s developers are committed to maintaining and iterating on the functionality of their malicious payloads, while simultaneously scaling the botnet across continents and cloud providers at a rapid rate,” Muir mentioned.
“It is expected that those behind the botnet are either waiting to implement additional functionality in the miner payload, or are intending to sell access to the botnet to other individuals or groups.”
Creator: data@thehackernews.com (The Hacker Information)
Date: 2023-09-21 08:51:00