NOTE: The next code examples have been contrived to supply detailed, illustrative representations of actual safety points I’ve discovered whereas reviewing code. They haven’t been pulled from precise codebases or commits. They’re written in Python and Ruby, however the ideas apply broadly.
1. Delicate Info in Log Recordsdata
Personally Identifiable Info (PII) is ruled by just a few completely different legal guidelines—GDPR in Europe and CCPA in California being the 2 most related examples on the time of publication, although extra laws will arrive on this subject over the subsequent few years. These legal guidelines govern the ways in which firms can retailer and use personally figuring out info, akin to names, bodily addresses, e-mail addresses, ID numbers, and the like. Usually, this laws requires that such info is saved securely. Logging is without doubt one of the largest violators of this requirement. Take the next instance:
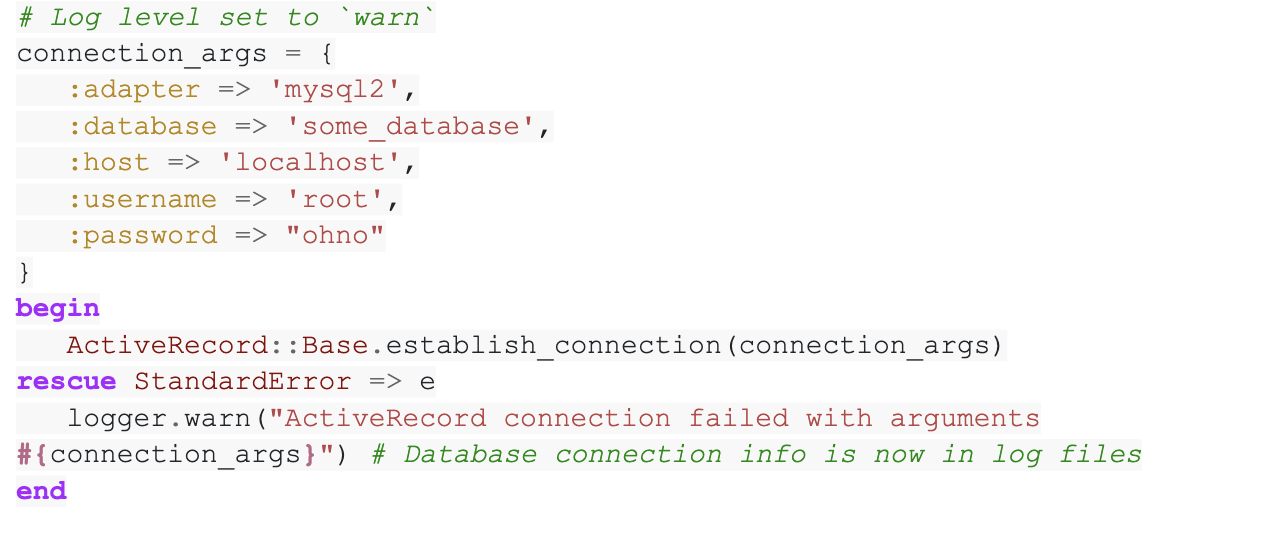
That is ostensibly cheap and protected, nevertheless it’s truly leaking e-mail addresses for customers into log recordsdata. What makes logging this info a safety concern? Logging programs are likely to not have the identical protections as a database. Attackers know this and may exploit it. The e-mail deal with within the above code needs to be changed by an obfuscated or encrypted Consumer ID quantity.
Secrets and techniques also can discover their approach into log recordsdata. Because the title implies “secret” keys are credentials that shouldn’t be uncovered, whereas some API keys are protected to reveal. I discover that lots of the chief offenders are database drivers that can print out your complete connection string on a connection failure. Sometimes connection makes an attempt for a few of these sadly misguided drivers needs to be wrapped in an exception handler that can swallow the error relatively than printing it to logs. Lesser offenders embody logging added by programmers for debugging functions which then sneaks right into a pull request or logging code that’s meant for the event surroundings that’s set with the flawed log degree.
2. Poor Cryptography Decisions
Sometimes this includes programs that use a one-time key or different token. I’ve seen occasions when people tried to take the straightforward approach out by doing a Base64 encoding of a timestamp (extremely guessable and in no way pseudo-random) or selecting a high-collision hash for a novel key (like md5) with out a distinctive constraint on the desk. Different failures embody utilizing encryption algorithms recognized to be insufficiently advanced for safety.
3. Inadequate Entry Controls
Also called Broken Access Control by OWASP. In 2021, Damaged Entry Management moved to #1 on the OWASP Top 10 listing of essentially the most important internet utility safety dangers.
Damaged Entry Management strikes up from the fifth place to the class with essentially the most severe internet utility safety danger; the contributed information signifies that on common, 3.81% of purposes examined had a number of Frequent Weak spot Enumerations (CWEs) with greater than 318k occurrences of CWEs on this danger class. The 34 CWEs mapped to Damaged Entry Management had extra occurrences in purposes than another class.
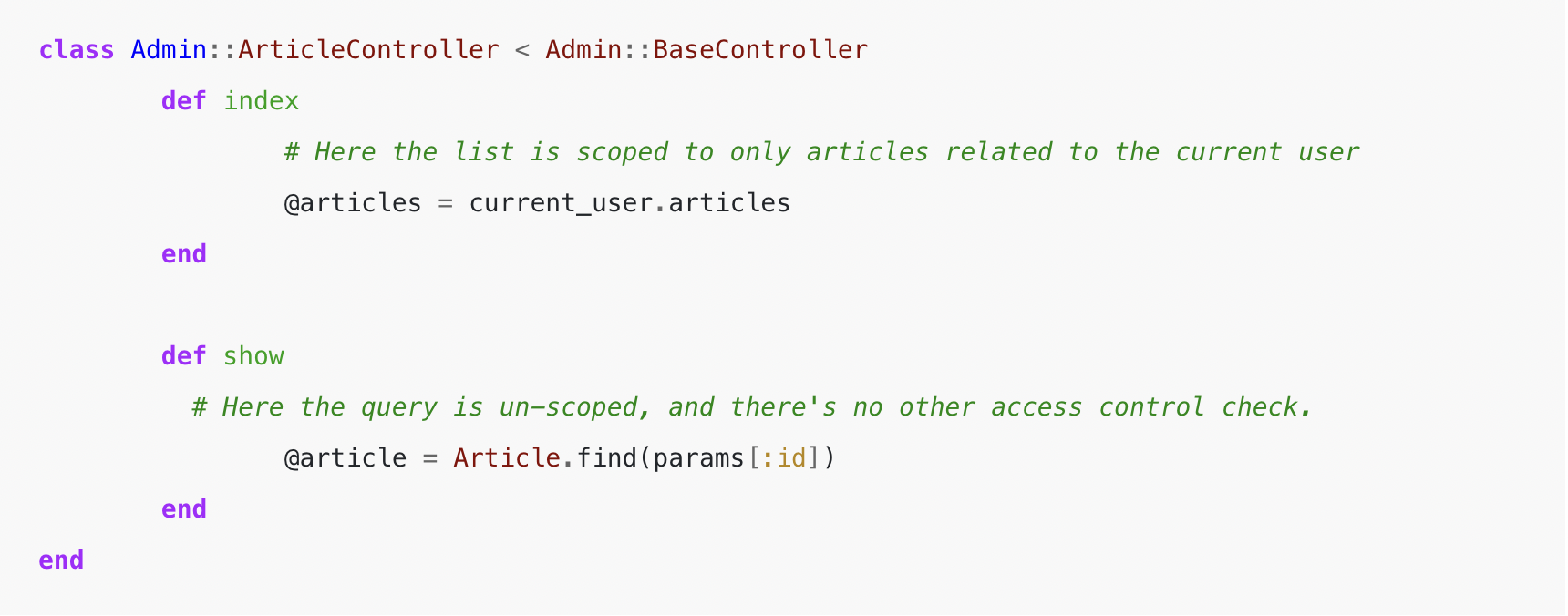
The commonest instance of that is associated to row-level safety, the place a consumer can entry a subset of the data in a desk. It’s straightforward to overlook so as to add a filter to a question or a verify to an endpoint, and it may be difficult to see the error within the UI of a program if the filtering is going on appropriately elsewhere within the code. That is most simply found by checking that the question filters on index actions are additionally current on all the different actions that function on particular person rows.
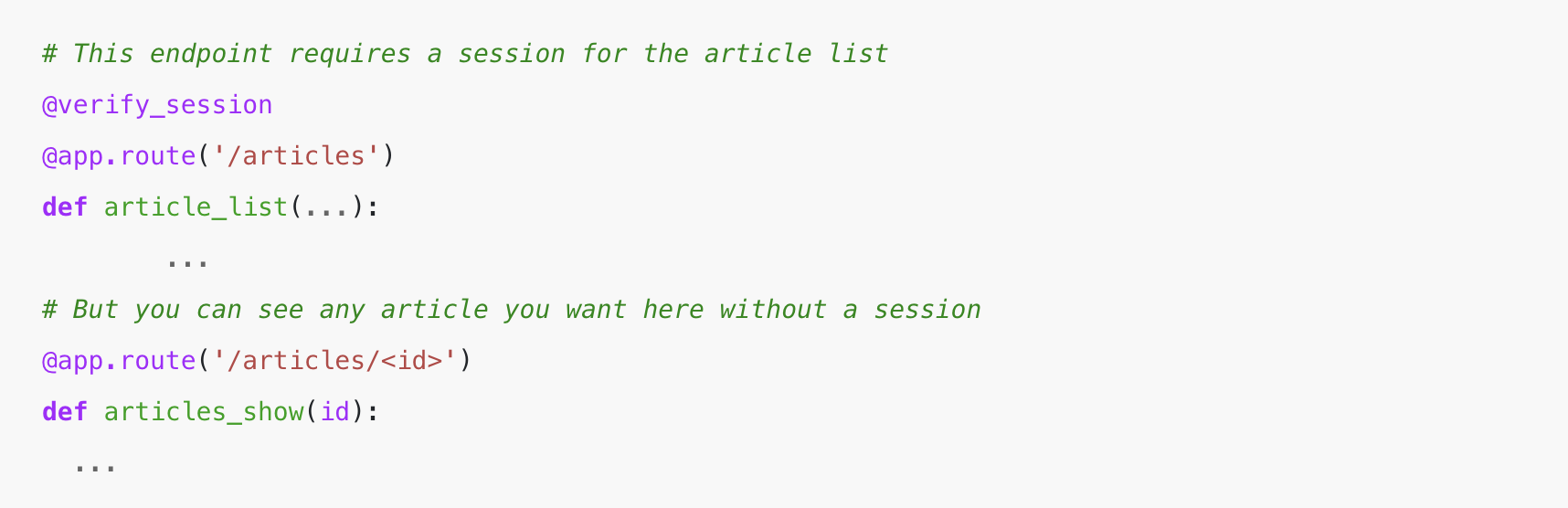
The opposite widespread entry management failure that I see is lacking session checks on endpoints—when, say, each endpoint requires a Python decorator to verify the session, it’s straightforward to depart that off. The most effective technique right here is to default every part to closed after which use decorators to open up entry as a substitute.
Extra about this here.
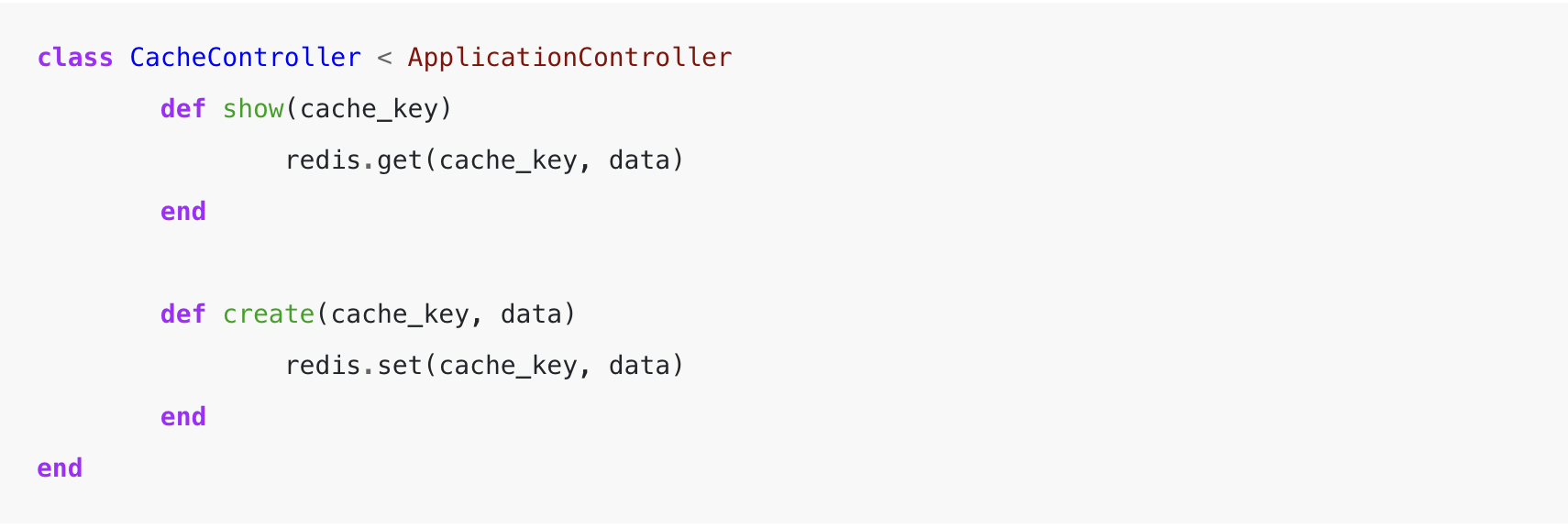
4. Unsecured Caches
A sample that I’m seeing increasingly, as single-page purposes change into extra advanced and customary, are cache layers uncovered to the front-end, the place any cache member is on the market to load if you already know the cache key. This could leak delicate info throughout periods and will outcome within the escalation of privilege assaults, notably if the session is used to retailer entry keys. When implementing front-end cache entry, it’s necessary to supply a system for limiting cache entry to solely these objects written by the present consumer, or if it’s a shared cache guaranteeing that the writes are verified server-side to keep away from injection assaults based mostly on unhealthy habits from customers.
5. Trusting the Consumer Too A lot
In case you’re new to improvement, you may consider the shopper because the “front-end” that customers work together with and the “back-end” because the programs that energy the front-end.
One of many first safety classes that I used to be taught was by no means to belief client-side enter; at all times validate that the shopper is doing what we count on it to do. I’m seeing increasingly situations of fewer server-side controls and extra reliance on the JavaScript front-end to supply information validation and management on consumer stream.
For instance, say an utility has a function the place customers can add photos. The front-end shopper could have validation to ensure a particular file is formatted to comprise the anticipated file kind (e.g., the file title ends in “.png”, “.jpg”), however this validation might be simply circumvented by an attacker searching for methods to insert an executable file right into a system. Placing an excessive amount of belief within the shopper for this validation opens a safety gap and alternative for the attacker to do that. The appliance’s back-end must also carry out validation that the file is the proper and anticipated kind.
Whereas I don’t have proof for this past private expertise, PullRequest offers engineers within the reviewer community like me a novel lens and perspective in reviewing code for a large number of engineering groups. And from what I’ve noticed, this can be a seen and rising pattern.
I consider the rise on this habits is a outcome, no less than partly, of the growing specialization within the business—internet improvement has change into more and more fragmented into front-end and back-end specialists and requires extra collaboration between the 2 teams to provide useful software program. When this collaboration isn’t going properly, there generally is a tendency for back-end considerations emigrate to the front-end, which may create safety vulnerabilities.
Conclusion
These 5 safety points are particularly necessary to catch in pull request code evaluate as they’re usually impossible to be caught in QA. They might be surfaced in a routine penetration take a look at (or pen take a look at) in case your group participates in these, however pen testing is often completed in longer length intervals whereas pull request code evaluate is very common, ongoing, and proactive—pen testing will often uncover safety points that exist already. Briefly, it’s a lot safer to catch safety points in code evaluate earlier than you, or an attacker discovers them in manufacturing.
If I had just one bit of recommendation that I might beam into each programmer’s thoughts, it could be to verify each single factor you write to logs for PII and secrets and techniques, in addition to each error you throw for a similar. That is the commonest recurring concern that I catch time and time once more.
This publish was initially revealed on the PullRequest web site. On April twenty eighth, 2022 HackerOne acquired PullRequest to assist energy developer-first safety testing options.
Discover publish writer Will Barrett here.
Author: William Barrett
Date: 2022-06-10 12:00:00



