libwebp exploit timeline
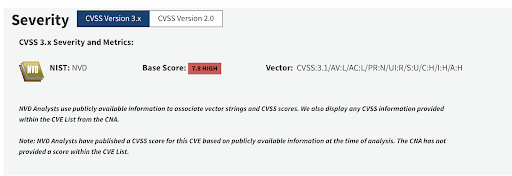
CVE-2023-41064; CVE-2023-4863; CVE-2023-5129
- A zero-click exploit implies that a consumer will not be required to click on something or take any motion to set off the exploit. Merely viewing a maliciously crafted WebP picture is sufficient to be contaminated.
- Citizen Lab researchers along with Apple’s Safety Engineering & Structure promptly disclosed the exploit to Google because of the potential injury to Google Chrome customers.
- On or round September 12 2023, Google reported the vulnerability to NVD as a Chrome vulnerability with a special id – CVE-2023-4863.
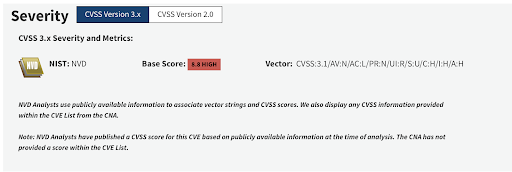
- On September 25, 2023 Google understood that the potential affect went past Chromium and submitted one other CVE with the id CVE-2023-5129giving it the utmost CVSS rating of 10.0. The scope was not restricted to a particular software program product or framework, quite it utilized to the libwebp library which is utilized by practically all fashionable working techniques. NVD marked this CVE as a reproduction of CVE--2023-4863.
What’s libwebp?
Libwebp is a well-liked library used to render webp pictures. This library is a part of virtually all fashionable working techniques and software program platforms, together with Apple iOS and Chromium primarily based merchandise like Google Chrome browser, Electron Software Framework, Debian (Free, Alpine), CentOS, Gentoo, SUSE and MacOS.
And merchandise like Google Chrome browser and the Electron Software program Framework are utilized in a number of the hottest functions together with Slack,1Password, Visible Studio Code, Discord and Microsoft Edge. You possibly can see a extra full checklist of applications using Chromium and applications using Electron by clicking on these hyperlinks.
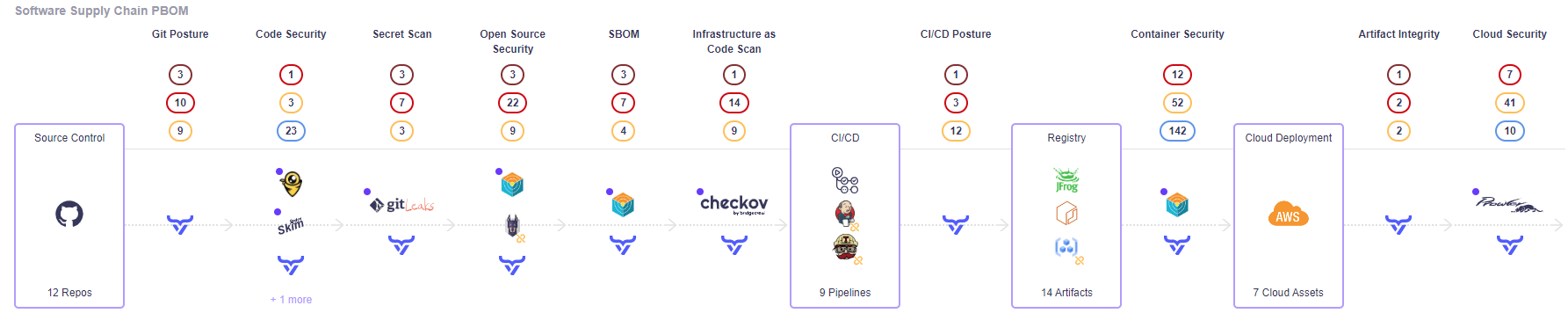
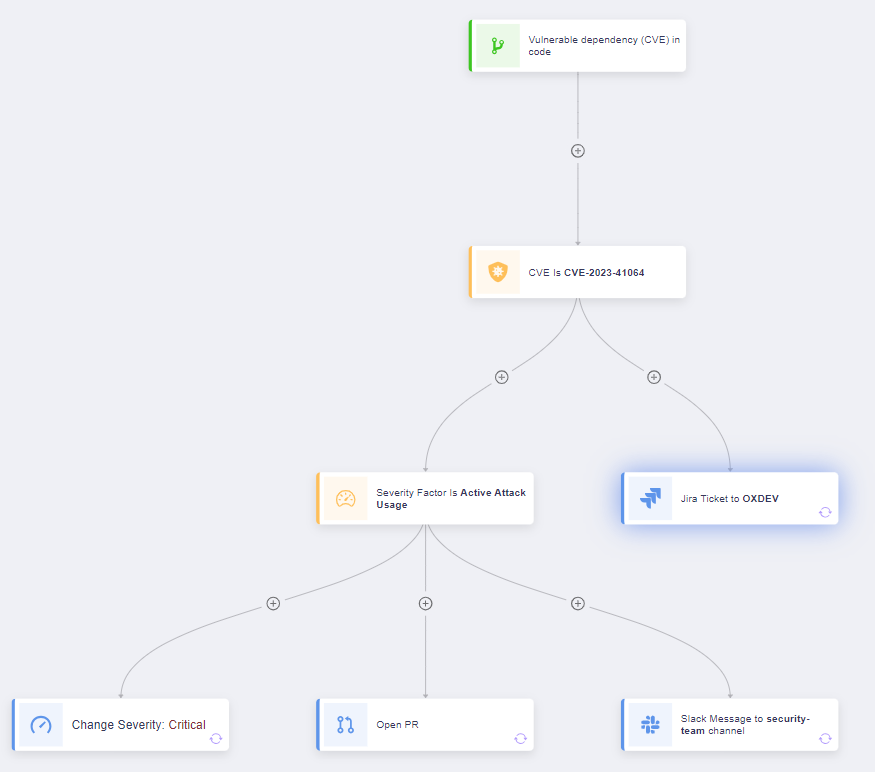
The best way to detect libwebp with OX Safety
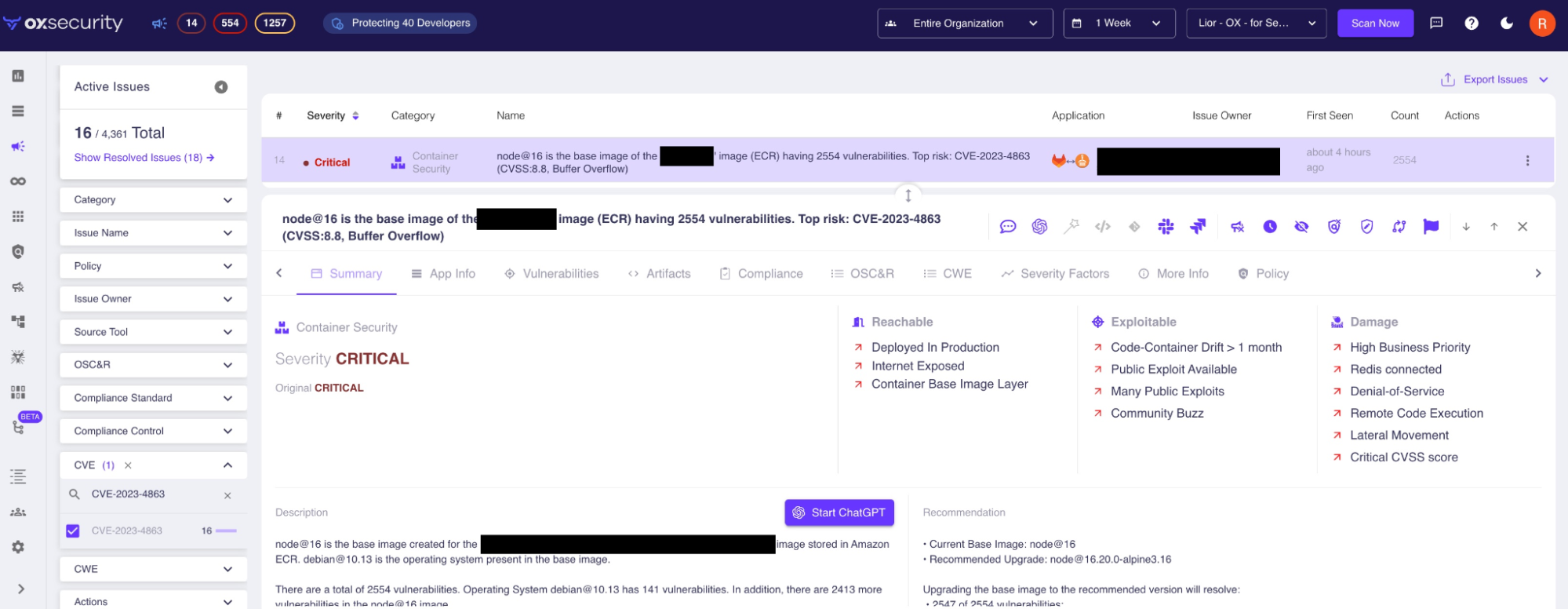
The libwebp vulnerability will be present in code, however it’s mostly detected in working techniques. This makes it notably tough to detect as a result of it requires safety groups to scan all working techniques in use, together with container base pictures. Conventional scanners sometimes don’t scan the latter.
For OX Safety customers, scanning Dockerfile definitions and container pictures occurs routinely.
What you must do now
Step 1: Take a look at your functions with OX Safety. Sign up for a free OX Security account.
OX Safety automates the remainder. Our answer:
- Scans all of your functions from cloud to code.
- Detects direct makes use of of libwebp, in addition to the harder problem of figuring out libraries, frameworks and base pictures that include libwebp.
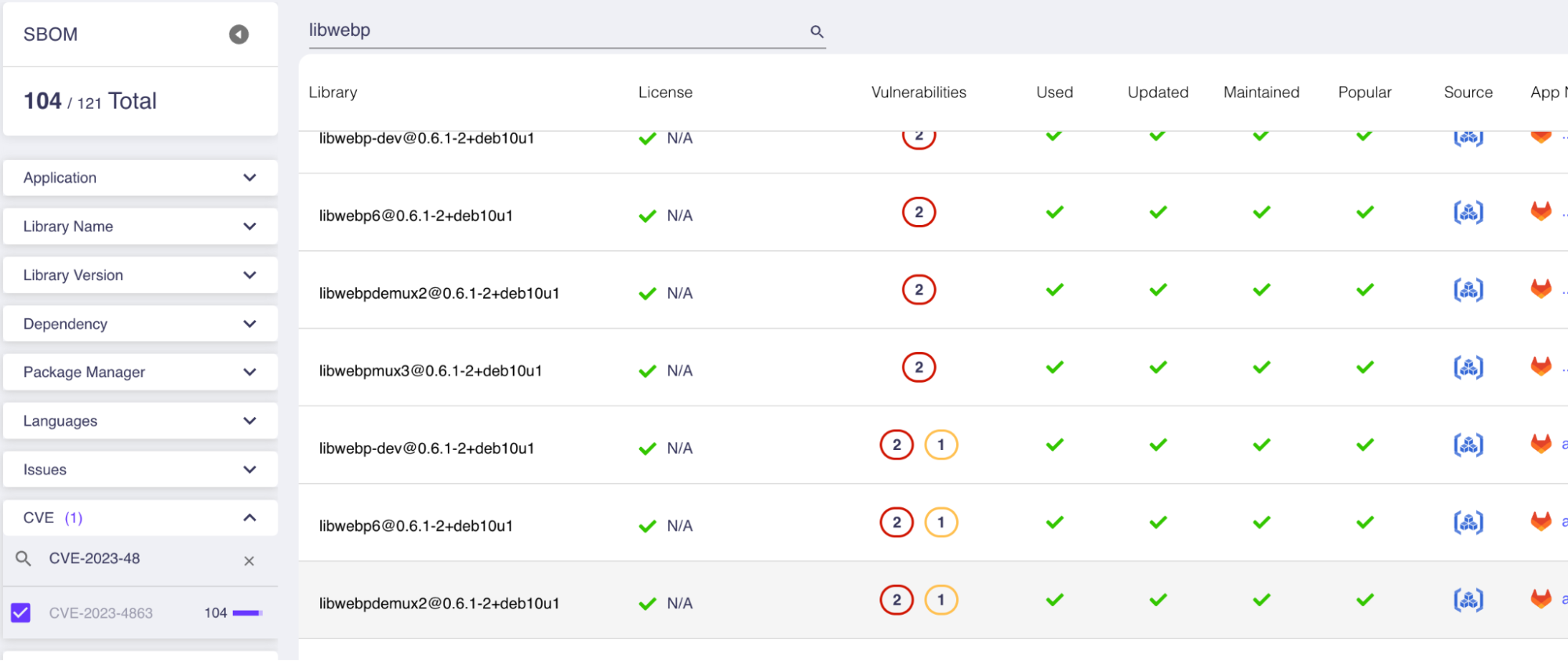
- Figures out the secure variations you have to be utilizing.

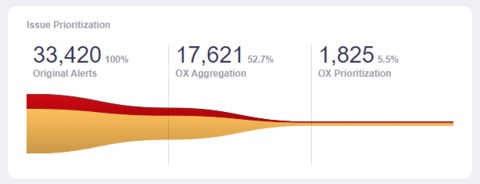
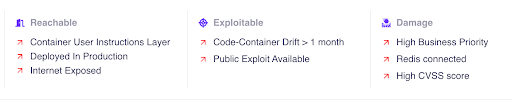
- Prioritizes dangers the place libwebp is uncovered in manufacturing and deprioritizes dangers the place libwebp will not be deployed or used.
- Triggers your group’s response plan.
OX Safety will proceed to observe this case and proceed to offer updates as occasions unfold. Be sure to follow us on Linkedin and examine again on the OX Security Blog for any developments as they happen. You probably have any questions please be at liberty to ship an e-mail out to one in all our product specialists at [email protected].
The put up What You Need to Know About the libwebp Exploit appeared first on OX Security.
*** It is a Safety Bloggers Community syndicated weblog from OX Security authored by Yael Citro. Learn the unique put up at: https://www.ox.security/what-you-need-to-know-about-the-libwebp-exploit/
Author: Yael Citro
Date: 2023-09-28 22:46:13