Pentesting has been round for many years, however it hasn’t undergone the revolution that different safety practices have. Organizations are likely to depend on pentesting as a software to simply “check-the-box” for compliance, slightly than one thing that really protects their model and clients.
Conventional pentesting engagements are sluggish, take up extreme bandwidth, and don’t ship impactful outcomes. On this weblog, I’ll take a look at the widespread errors organizations make with their pentests and present how by leveraging the facility of the pentester group and the effectivity of a Pentest as a Service (PTaaS) platformpentesting can add actual worth to your group.
Downside 1: Pententers Are Inexperienced
When clients inform me about their experiences with conventional distributors, they point out that they typically don’t get a whole staff of skilled pentesters. As a rule, they get a staff principally composed of junior pentesters with restricted expertise who work with a extra senior pentester with extra expertise. In consequence, the senior pentester is pressured to separate their time between testing, instructing, and reporting, and the client doesn’t get the total worth.
HackerOne pentesters are an elite subset of our group that’s hand-selected and vetted by our Neighborhood staff. As a part of the vetting course of, the Neighborhood staff evaluates their previous skilled pentest expertise, their efficiency on different HackerOne packages, and their certifications and different credentials. Because of the excessive requirements we preserve for our pentesters, 65% of our group has over 5 years of expertise with pentesting. Which means that our clients are getting skilled, credentialed testers with each pentest.
Downside 2: Pentesting Is Too Guidelines-Pushed
Pentesting is methodology-driven by nature, however oftentimes conventional pentest companies are extra centered on shifting via a guidelines than really discovering vulnerabilities. As a result of most of our Pentest Neighborhood additionally participates in Bug Bounty Programsthey’re used to considering like a real-world adversary and figuring out hard-to-find vulnerabilities in your techniques earlier than criminals do. We additionally encourage this creativity by budgeting unstructured testing time to go alongside the time budgeted for the HackerOne pentest methodology.
Downside 3: Restricted Pool of Expertise
Prospects are used to rotating conventional pentest distributors with a purpose to get a recent perspective on the property they’re testing. It is because these distributors sometimes don’t have a deep bench of expertise, which means the one method to get a brand new perspective is to herald one other vendor. Nonetheless, bringing on different distributors signifies that the safety staff has to spend time getting them onboarded and reduces their concentrate on enhancing the safety of their merchandise.
Due to HackerOne’s group mannequin, now we have a whole lot of pentesters on our bench. Which means that our clients can rotate pentesters to get a recent perspective, with no need to onboard one other vendor. Due to the depth and breadth of expertise amongst our pentesters, they’ve a broad vary of expertise throughout many various kinds of property and vulnerability lessons. Which means that we are able to supply the suitable expertise for our buyer’s assessments in a brief time frame. By leveraging skilled safety researchers for pentesting, 20% of HackerOne vulnerability findings in a pentest are excessive or essential severitywhich is roughly double the business commonplace.
Downside 4: Sluggish Time To Outcomes
Organizations are sometimes pissed off with the period of time it could possibly take to kick off a pentesting program and obtain tangible outcomes.

The time it takes to establish and report vulnerabilities is among the most typical complaints of pentesting. Trade-standard pentests take not less than two weeks after the pentest concludes to get outcomes collectively and ship them to the client. With HackerOne’s pentests:
- 77% of our clients discover a vulnerability inside 24 hours of launch
- 54% of our clients obtain a vulnerability discovering inside three days of a take a look at launch
Due to our PTaaS platform, clients additionally obtain these vulnerability findings in actual time. Which means that oftentimes they’ve remediated the vulnerability and had it retested by the point that the pentest concludes.
Downside 5: No Visibility All through The Course of
One other constant shortcoming of pentesting is the shortage of visibility into real-time exercise and outcomes. Many organizations don’t have entry to a centralized location via which to view efficiency and talk with pentesters.

Our group of pentesters studies their findings utilizing the HackerOne PTaaS platform. The platform provides our clients real-time visibility into the progress of every pentest, in order that they perceive the place a pentest is at any given cut-off date. Prospects additionally handle all facets of their pentest engagements via the platform, from scoping to testing and reporting to remediation. This makes it very straightforward for our clients to launch a pentest rapidly as a result of it’s all carried out out of the platform, slightly than coordinated through back-and-forth emails.
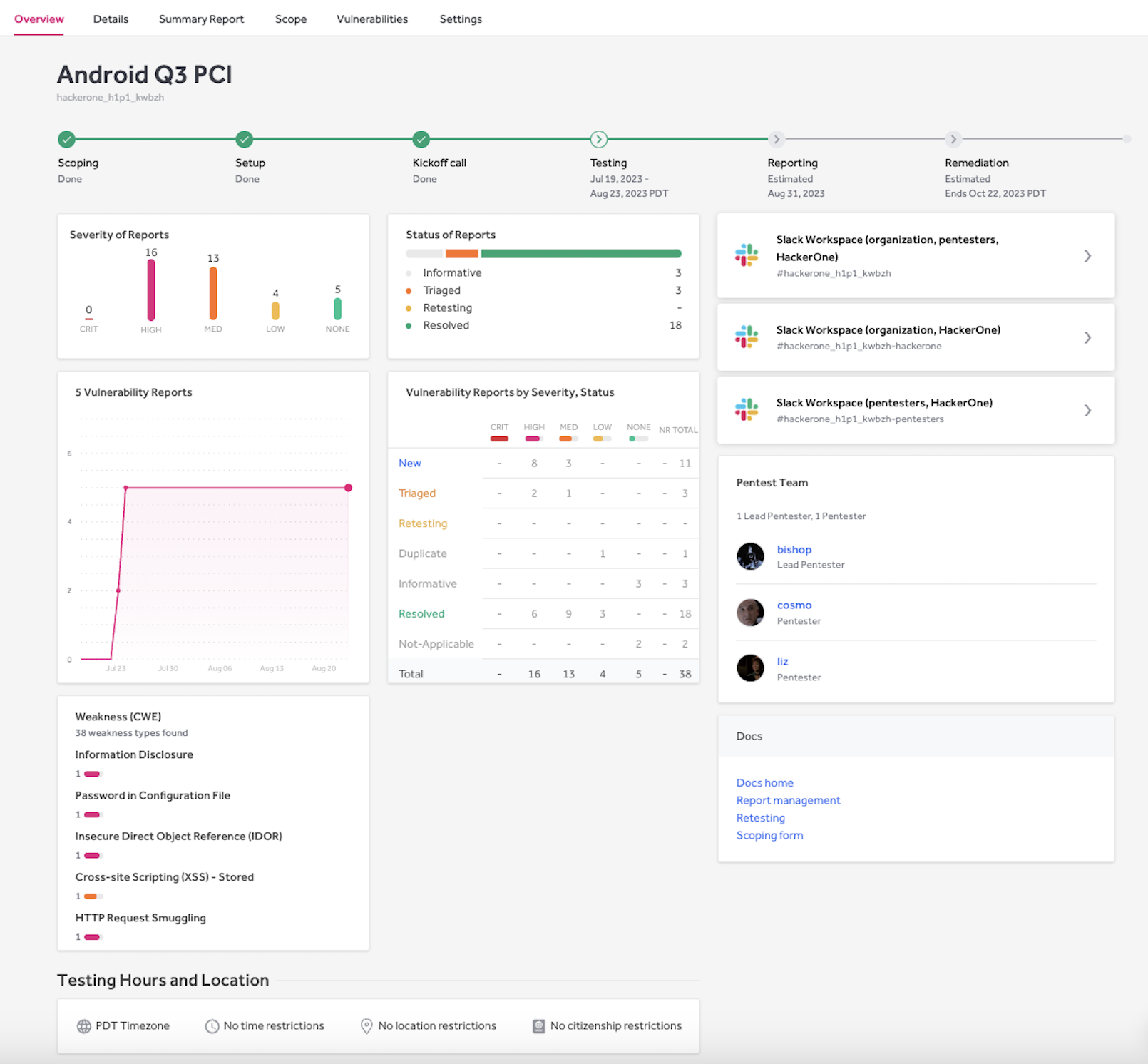
Downside 6: Lack of Communication With Pentesters
A conventional pentest tends to be a black field within the sense that there’s little or no communication that occurs all through the take a look at. The take a look at kicks off and runs for just a few weeks, concludes, after which a report is delivered a few weeks after that.
With HackerOne’s Pentest, these accountable for their group’s pentests have a direct line of communication with each the pentesters and our Technical Engagement Managers, who handle the pentest, through Slack. You get common standing updates out of your pentest staff, and the open communication helps the assessments run effectively.
Downside 7: Pentesting Isn’t Built-in With Remediation
Even with a streamlined platform and communication with pentesters, the outcomes are solely pretty much as good as a corporation’s potential to rapidly and effectively tackle vulnerabilities. This requires considerate integrations into ongoing instruments and processes.
For organizations that wish to combine with their ticketing techniques and different SDLC toolsthe platform provides over 20 bidirectional, purpose-built integrations, plus APIs so as to add extra. This helps streamline the remediation process- no extra copying and pasting vulnerabilities from a PDF report with a purpose to get them to your growth staff for a repair!
Mix the Comfort of PTaaS With the Energy of the Pentest Neighborhood
Combining the safety experience of our pentester group with the efficiencies of our PTaaS platform reduces menace publicity throughout your assault floor. Maybe most significantly, we discover clients actually worth the direct engagement and sensible data that comes from working with our expert pentesters. It energizes and educates safety groups as a result of it’s a really interactive and clear course of.
When you’d wish to see how our pentesters can uplevel your pentest program or your broader safety program, reach out to the team at HackerOne.



