Introduction
Within the evolving panorama of blockchain and cryptocurrency, new assault vectors and scams proceed to emerge, focusing on unaware customers. One of many latest scams is the “Zero-Value Token Transfer Phishing Attack,” affecting customers on networks like TRON and Ethereum.
This evaluation goals to make clear how the assault works, illustrate a pattern assault state of affairs, focus on mitigation methods, and draw upon real-world examples. The target is to lift consciousness and arm customers with the information to guard themselves.
Instance Assault Situation
Stage 1: Figuring out the Sufferer
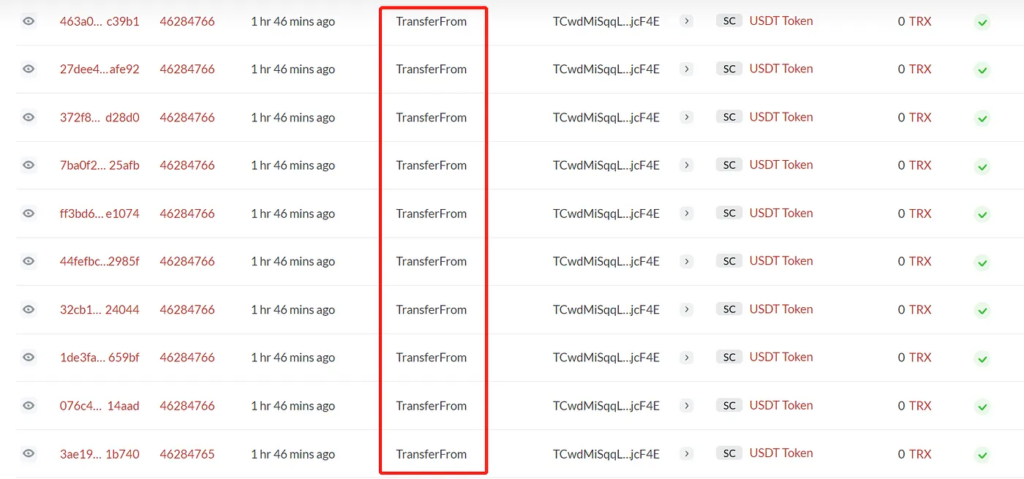
The attacker screens on-chain logs for token switch occasions. When a switch happens, the attacker singles out the sender’s deal with because the potential sufferer and the recipient’s deal with for spoofing.
Stage 2: Making a Spoofed Tackle
The attacker makes use of instruments to generate a conceit deal with that intently resembles the recipient deal with. The self-importance deal with retains the identical first and previous couple of characters of the recipient’s deal with to mislead the person into considering it’s the identical, legit deal with.
Stage 3: Triggering a Zero-Worth Switch
Using the transferFrom technique obtainable within the ERC-20 token implementations, the attacker broadcasts a specifically crafted transaction. The transaction reveals a switch of 0 tokens from the sufferer’s deal with to the spoofed deal with, bypassing the necessity for approval as a result of zero worth.
Stage 4: The Lure
The sufferer, upon seeing the brand new deal with of their transaction historical past, is deceived into considering that they’ve handled this deal with earlier than. They may then use this spoofed deal with for future transactions.
Mitigation Methods
For Customers:
- Confirm Full Addresses: At all times confirm the whole deal with, character by character, earlier than initiating any transaction.
- Test Supply: Be cautious about copying addresses from transaction histories, particularly these you didn’t provoke.
- Make the most of Safe Wallets: Use wallets that flag or filter out malicious transactions and addresses.
For Pockets Suppliers and Blockchain Explorers:
- Zero-Worth Flagging: Flag or filter transactions the place the switch quantity is zero.
- Tackle Collision Detection: Implement algorithms to detect self-importance addresses which can be too much like legit addresses.
- Consumer Alerts: Alert customers about new or unknown addresses when initiating transfers.
Actual-world Situations
- Case 1: In February 2023, this assault led to the lack of $19 million in sufferer funds from varied pockets suppliers
Conclusion
The Zero-Worth Token Switch Phishing Assault exploits person habits and current belief in blockchain historical past logs to deceive customers into sending belongings to an attacker’s deal with. As crypto adoption grows, customers must be vigilant and conscious of such refined assault vectors. Security measures should be constantly up to date to guard in opposition to rising threats.
Author: ImmuneBytes
Date: 2023-08-31 04:32:00