Based on Transforma Insights, the large type of Web of Issues (IoT) units in use globally is predicted to almost double from 15.1 billion to 29 billion in 2030. These devices can be found in all kinds of bureaucracies, together with good vehicles, smartphones, well being video displays, alarm clocks, and favourite household residence home equipment like espresso makers and fridges. Making certain every instrument is correctly succesful and in a position to deal with growing workloads is a significant concern for producers and resolution suppliers within the IoT house. That is the place IoT testing comes into play, making certain that IoT units and methods not solely fulfill their particular necessities but additionally present the anticipated degree of efficiency.
Why is IoT Testing Necessary?
There’s a saying in hacking, if it’s within the cloud it could possibly rain wherever. Meaning should you can entry the gadget from the web then anybody can. It’s discoverable by different menace actors and likewise can provide unauthorized entry.
In our inner analysis, we’ve got discovered that many good buildings are simply accessible from the online.
(Constructing administration resolution uncovered on web)
Throughout our pentest our group discovered most of them had been operating on the susceptible software, utilizing default settings and credentials which might be discovered on the web site of the IoT product.
( Sensible Constructing software program susceptible to misconfiguration)
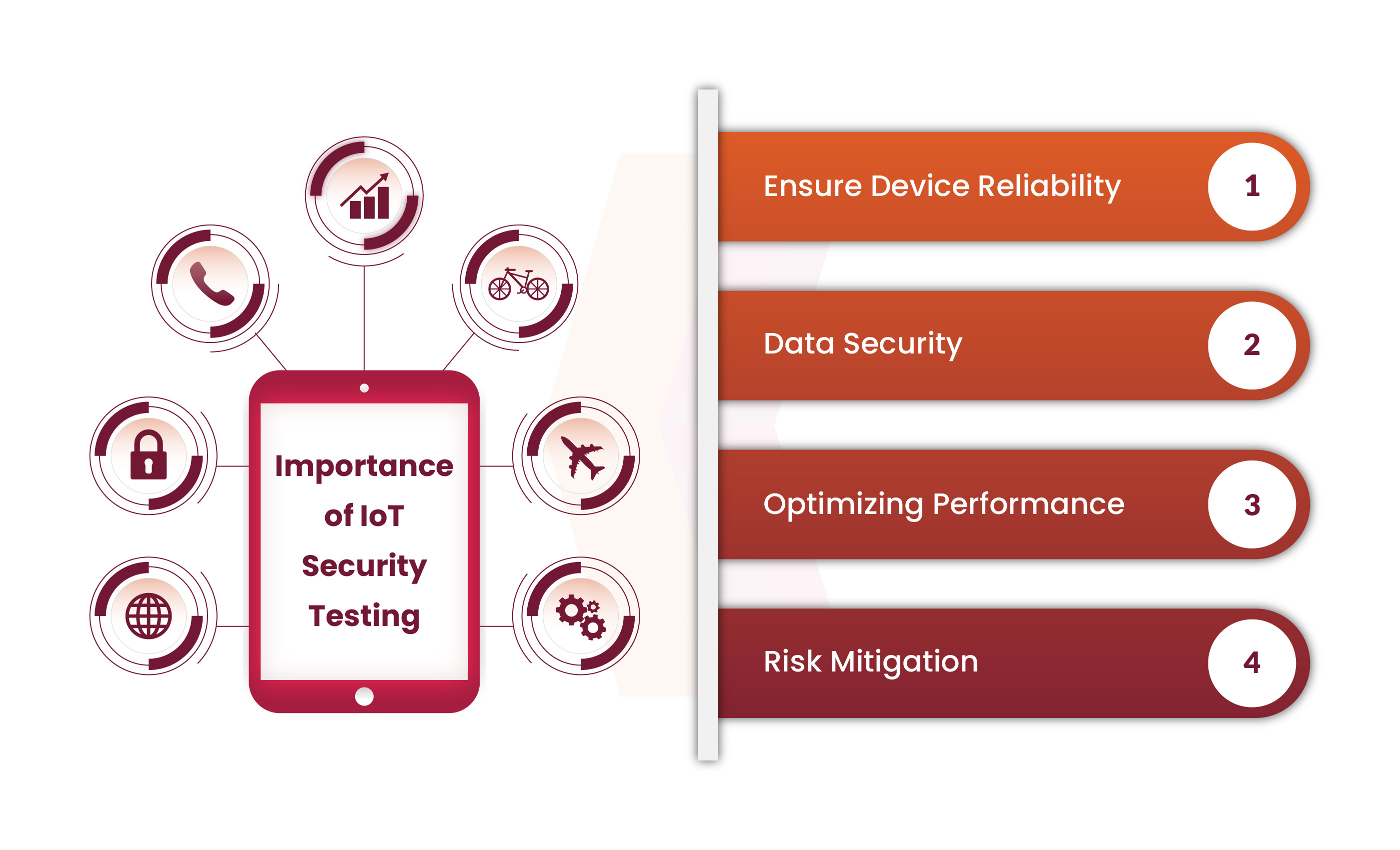
Listed here are key explanation why IoT testing is necessary:
Guarantee Gadget Reliability
Web of Issues (IoT) units are important to each every day residing and enterprise operations. Testing is important to make sure that these units function constantly beneath a spread of circumstances and to scale back the danger of faults or breakdowns that might probably interrupt necessary operations.
Knowledge Safety
IoT units continuously ship delicate information, so it’s vital to offer robust safety measures a prime precedence. Testing is an important instrument for figuring out gaps and vulnerabilities in a instrument’s safety measures, offering a buffer in opposition to system failures that would jeopardize consumer privateness or information.
Optimizing Efficiency
Testing makes it attainable to judge an Web of Issues (IoT) gadget’s efficiency in a wide range of situations, together with response occasions, the effectiveness of information transmission, and commonplace functioning. Efficiency optimization is crucial to make sure decreasing the danger of sluggish response occasions.
Danger Mitigation
IoT testing is crucial for decreasing the dangers linked to IoT units, equivalent to information loss or safety vulnerabilities. Proactively detect and eradicate dangers to help organizations in enhancing the reliability and validity of IoT options.
Challenges in IoT Testing and Answer to Overcome Them
Beneath are efficient methods to sort out these challenges:
Safety Issues
Safety points persist as a distinguished problem within the IoT panorama. The growing variety of IoT units makes them more and more enticing targets for attackers. Setting data and gadget safety as a prime precedence will help stop functionality breaches. IoT testing safety challenges and difficulties embody client passwords, unpatched vulnerabilities, hacks, information theft, and lots of extra.
Answer
- Conduct complete safety testing, which ought to contain IoT penetration testing and vulnerability assessments.
- Incorporate safe communication protocols equivalent to TLS/SSL and strong authentication mechanisms.
- Persistently replace the firmware and software program of units to deal with and patch safety vulnerabilities.
Privateness Points
Inside the spectrum of IoT testing challenges, a various vary of issues emerges, with specific emphasis on privateness points in at the moment’s digital panorama. The numerous problem lies in navigating the fragile steadiness between gathering information from IoT units and respecting the privateness of customers. Listed here are some key factors equivalent to information assortment sensitivity, consumer consent, compliance, and way more.
Answer
- Guarantee adherence to compliance and requirements
- Incorporate efficient information and encryption protocols.
- Implement information anonymization, encryption, and clear privateness insurance policies
Scalability
Scalability is a significant IoT problem as a result of surging variety of units. Managing IoT infrastructures turns into advanced, spanning information storage, processing, and gadget integration. Dealing with the colossal quantity of generated information requires scalable storage options, whereas processing energy should scale for real-time insights. Integrating various IoT units into present methods poses extra complexity because the panorama evolves.
Answer
- Conduct scalability testing to pinpoint hindrances and optimize the system structure.
- Incorporate load-balancing mechanisms for the even distribution of site visitors.
- Implement IoT safety testing for dynamic scaling in response to demand.
Following Compliance
Making certain compliance, particularly with strict frameworks like GDPR, is essential for increasing IoT safety testing operations. Adherence calls for meticulous information dealing with, consumer consent, and privateness safety. Incorporating compliance into IoT improvement is important, involving strong encryption, clear information practices, and proactive measures to mitigate dangers and keep consumer belief. Non-compliance can result in extreme penalties, emphasizing the significance of constructing regulatory adherence a core precept for sustainable IoT development.
Answer
- Keep up to date on relevant laws and requirements within the areas the place the IoT resolution is about to be applied.
- Incorporate testing for compliance
- Coordinate with authorized and compliance groups to make sure alignment with regional necessities.
E-book a Free Session with our Cyber Safety Consultants

Greatest Practices for IoT Testing
Adhering to IoT gadget safety finest practices is essential for steady consumer, gadget, and information safety. The technique ought to define safety measures, their implementation, and ongoing monitoring. Listed here are a number of IoT safety testing finest practices:
IoT Endpoint Safety
Securing IoT units includes an important step: hardening via IoT endpoint safety. This course of contains addressing vulnerabilities in high-risk ports like Transmission Management Protocol (TCP) and Person Datagram Protocol (UDP), securing wi-fi connections, and making certain encrypted communications. Safety in opposition to malicious code injection can be important.
Organizations could safeguard their networks from superior threats, equivalent to ransomware and malware, by placing endpoint safety into place. Units on the neighborhood edge are strengthened, giving security personnel complete visibility, instantaneous insights into linked units, and a smaller assault floor.
IoT Gateway Safety
Enterprises can improve IoT gadget safety via IoT gateway safety, imposing web entry insurance policies, and blocking unauthorized software program, like malware. A Safe Net Gateway (SWG) with options equivalent to software management, thorough HTTPS and SSL inspection, distant browser isolation, and URL filtering is essential, particularly as organizations migrate to the cloud and allow distant connections. This helps stop safety dangers for web-based site visitors, safeguarding IoT units from exterior and inner cyber threats. Moreover, using menace monitoring options prevents information leaks, whereas digital personal networks (VPNs) encrypt searching information, securing customers’ web exercise from potential hacker snooping.
Securing Cloud API
Cloud software programming interfaces (APIs) facilitate communication and integration for IoT purposes and methods, enjoying an important position in connecting providers and transferring information. The potential penalties of a compromised or hacked API are extreme, resulting in a big information breach. Therefore, making certain the safety of cloud APIs is paramount, achieved via measures equivalent to authentication, encryption, tokens, and the implementation of API gateways. As an example, net API safety safeguards information throughout transmission throughout the web, whereas REST APIs make use of encryption for information and web connections, making certain the safety of shared data between servers and units.
Safety of Knowledge Storage
As IoT units and sensors generate escalating quantities of delicate information, encompassing monetary, private, and biometric data saved in cloud-based or {hardware} storage options, the implementation of strong safety measures turns into paramount. Making certain the safety of this data throughout storage or switch is essential. Securing information storage includes the utilization of environment friendly and up-to-date antivirus options, together with monitoring and scanning instruments that comprehensively tackle real-time IoT threats throughout the community. Important options embody versatile reporting and scanning capabilities, notification methods, antimalware protocols, and a centralized administration console that gives in-depth visibility into community exercise.
Conclusion
The fast growth of IoT units calls for strong IoT testing methodologies to deal with safety, privateness, scalability, and regulatory compliance challenges. Implementing measures equivalent to endpoint safety, gateway safety, securing cloud APIs, and safeguarding information storage is essential. Proactively adhering to regional laws and embracing finest practices in IoT safety testing is crucial for sustainable development. Organizations can develop resilient IoT methods that fulfill consumer expectations via addressing obstacles and incorporating optimum methodologies.
Cratical, being a CERT-In empanelled auditor performs an important position in delivering top-notch safety providers. We presently work with 400+ SMEs and 150+ massive firms. Leveraging our intensive experience, we provide complete evaluation and strong protection mechanisms to counter the persistent menace of cyber assaults. Participating with critical allows immediate identification and determination of safety vulnerabilities, successfully thwarting malicious hackers from exploiting weaknesses.
The submit IoT Testing: Best Practices And Challenges in 2024 appeared first on Critical Blogs.
*** This can be a Safety Bloggers Community syndicated weblog from Critical Blogs authored by Shikha Dhingra. Learn the unique submit at: https://kratikal.com/blog/iot-testing-best-practices-and-challenges-in-2024/
Unique Put up URL: https://securityboulevard.com/2024/02/iot-testing-best-practices-and-challenges-in-2024/
Class & Tags: IOT,Safety Bloggers Community,Cyber Safety – IOT,Safety Bloggers Community,Cyber Safety
Author: CISO2CISO Editor 2
Date: 2024-02-09 00:46:20



